Vulnerability Management Detection & Response (VMDR) FAQs & Resources
Here you will find answers to the common, high-level questions about this foundational cyber security process as well as links to VMDR resources that we have hosted on our website.
Vulnerability management programs must continue to evolve to match these rapidly changing environments. Adopting a risk-based approach to vulnerability management will help teams prioritize their efforts and align the program with organizational goals.
Vulnerability Management Survey
VMDR FAQs
What is Vulnerability Management, Detection and Response?
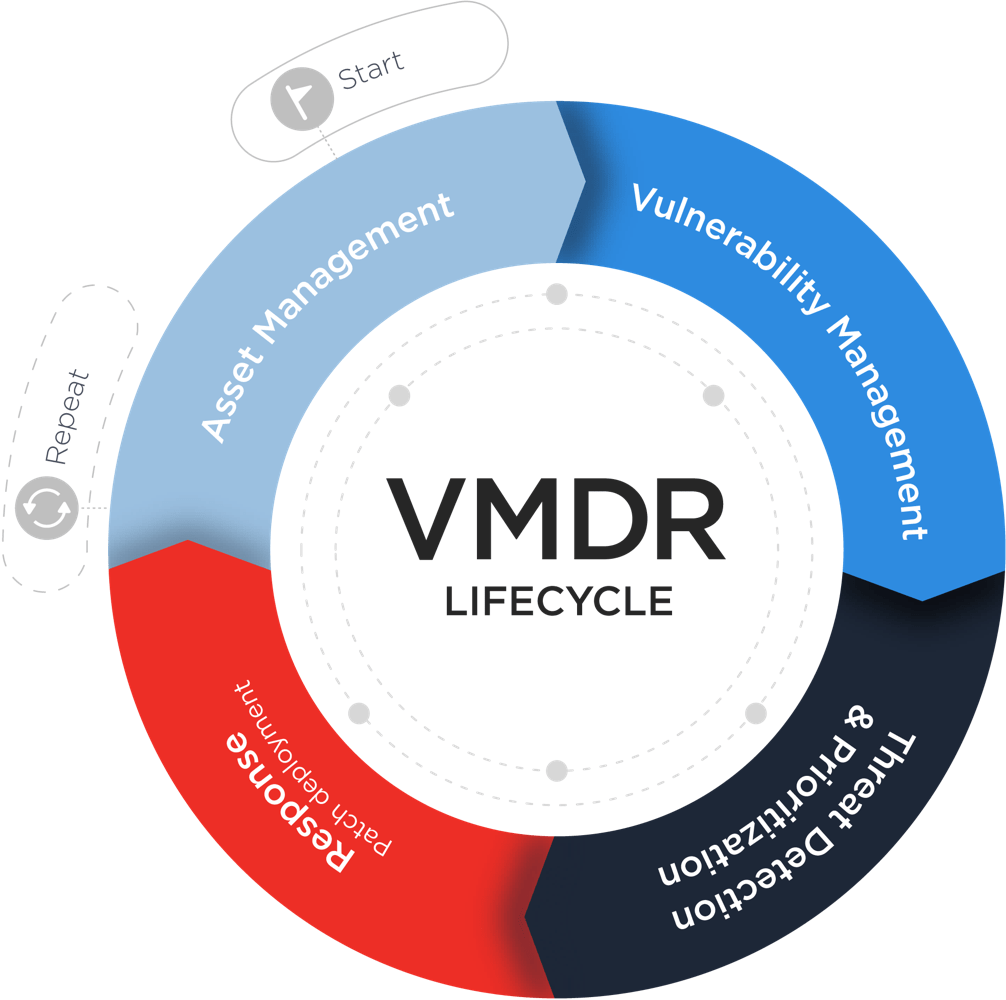
Vulnerability Management, Detection and Response (VMDR) establishes the cyber security foundation that today’s hybrid, dynamic and distributed IT environments require. It’s a continuous, seamlessly orchestrated workflow of automated asset discovery, vulnerability management, threat prioritization, and remediation. By adopting the VMDR lifecycle, organizations decrease their risk of compromise by effectively preventing breaches and quickly responding to threats.
In this way, organizations can safely pursue and extend their digital transformation, which has become essential for boosting competitiveness. As SANS Institute’s Andrew Laman reminds us, cybersecurity must never be an afterthought, even as technology evolves and helps organizations be agile and customer-centric.
Why do we need Vulnerability Management, Detection and Response?
It's simple. You can’t protect what you can’t see.
IT environments no longer have well-defined perimeters. Their security posture has become porous as organizations adopt innovations like cloud computing, containers, mobility and DevOps. You can’t protect this blurred perimeter with a mishmash of disparate tools that don’t interoperate. That creates data silos, opens up gaps, creates tactical uncertainty, and slows you down.
Increased complexity.
As Forrester Research blog post The Impact Of Digital Transformation On The Vulnerability Management Space states, this increased complexity generates a need for better asset management and prioritization of remediation workloads. "Many organizations become overwhelmed to the point of having to figure out what actually has to get done; this is the foundation of the vulnerability risk management space."
The 4 pillars of Vulnerability Management, Detection and Response
Vulnerability Management, Detection and Response has four core components that form the basis for an integrated, risk-based breach prevention and response program.

IT Asset Management

You can’t secure what you can’t see. It’s essential to have a complete, updated global inventory of all assets across your network: on prem, endpoints, clouds, containers, mobile, OT and IoT — everywhere. This continuous discovery process must detect all assets — approved and unapproved — and collect granular details about each, such as installed software, hardware details and running services.
Asset data should be normalized, and assets automatically categorized with dynamic rules-based tagging. This classification context helps assess risk. For example: Does this server contain a database with customer data? Must this asset comply with PCI? Is this the CEO’s laptop? The inventory should be easy to query, and to drill down into, as well as be bi-directionally synchronized with your CMDB, giving you a consistent, single source of truth for all your assets.
The importance of asset management can’t be overstated. “Asset management is critical to everything we do as security professionals,” Forrester’s Josh Zelonis wrote in his blog post Introducing Forrester’s Asset Intelligence Model (AIM) For Asset Management.
Vulnerability Management

The traditional “scan-the-network” approach doesn’t scale well for modern IT infrastructure. Therefore all assets — on premises, in public clouds, on endpoints — must be checked for vulnerabilities and misconfigurations continuously, using active, authenticated scans, passive network analysis and, even better, lightweight agents that reside on the assets and detect and report any changes in real time. This Vulnerability Management, Detection and Response phase also includes assessment of digital certificates and TLS configurations.


Vulnerability Detection and Prioritization

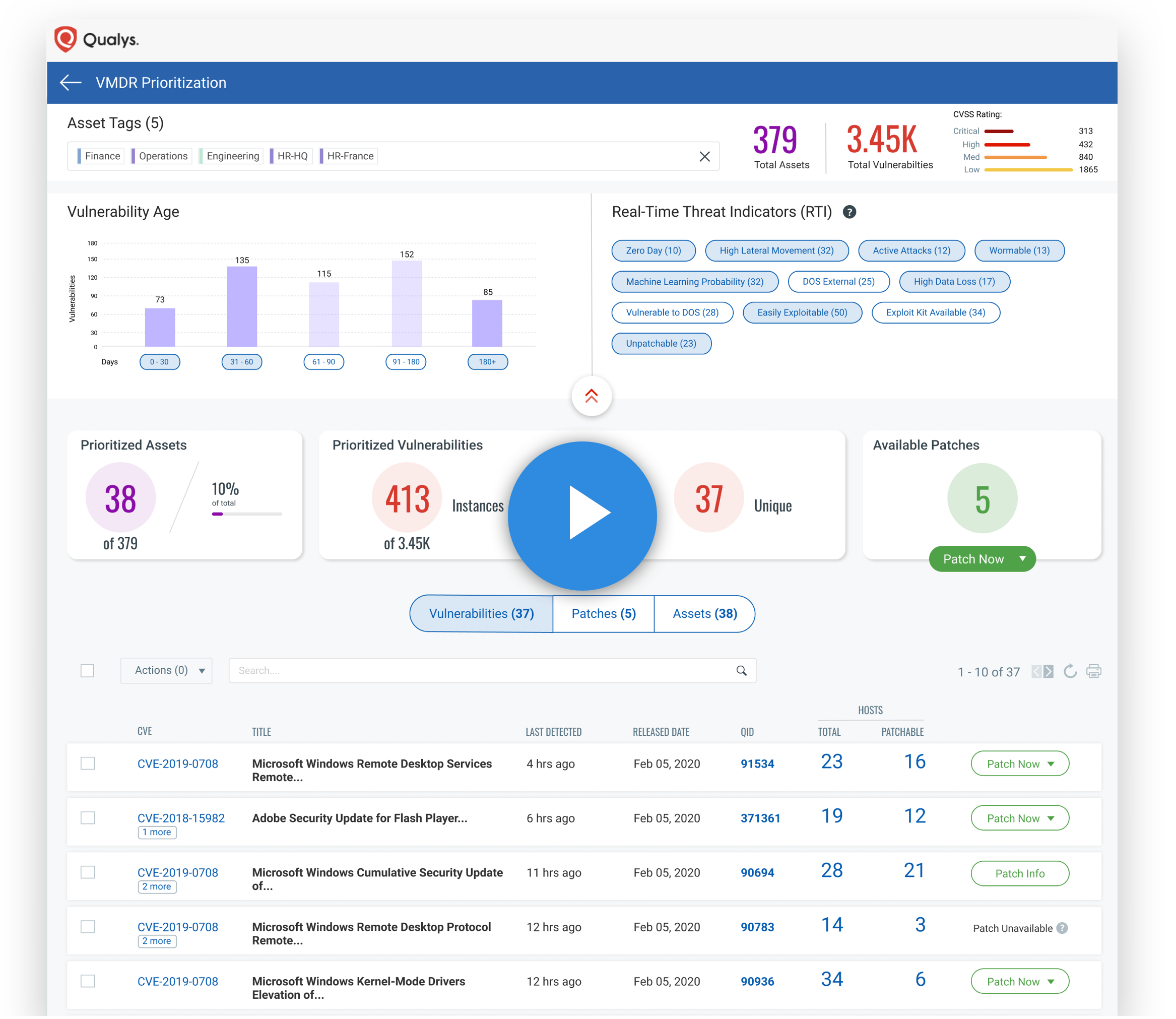
Vulnerability Management, Detection and Response leverages the latest threat intelligence, advanced correlation and machine learning to pinpoint the riskiest vulnerabilities on the most critical assets. VMDR highlights indicators of compromise, and leverages ML to surface potentially severe vulnerabilities. That way you can prioritize which threats to mitigate first, before attackers exploit them.
"One of the most common ways to fail at Vulnerability Management is by simply sending a report with thousands of vulnerabilities to the operations team to fix," wrote Gartner analyst Augusto Barros in the blog post The New Vulnerability Management Guidance Framework. "Successful VM programs leverage advanced prioritization techniques and automated workflow tools to streamline the handover to the team responsible for remediation."
Vulnerability Remediation

Vulnerability Management, Detection and Response identifies the most appropriate remediation for each threat, whether it’s deploying a patch, adjusting a configuration, renewing a certificate or quarantining an asset. If patching is the course of action, an effective VMDR solution will automatically correlate vulnerabilities and patches, and select the most recent patch available for fixing a particular vulnerability in a specific asset. With VMDR, remediation is fast, precise and smooth — all critical elements when a delay can give attackers a chance to breach your defenses.
By combining these four core elements, a VMDR process allows security teams to make decisions and take actions that are based on data-driven risk assessments. "Organizations need to implement a risk-based approach in their programs, so they are doing more than just determining the criticality rating of a vulnerability," explains SANS Institute’s Jake Williams in the paper Why Your Vulnerability Management Strategy Is Not Working and What to Do About It.

What are the Benefits of VMDR
-
Reduced time to remediate (TTR)
Infosec teams must stay a step ahead of attackers. Every day that a critical vulnerability remains unaddressed increases the chances that an attacker will exploit it. "When a security incident occurs, various clocks begin ticking," SANS Institute’s Matt Bromiley explains in the paper Detecting Malicious Activity in Large Enterprises. "The more time an attacker has in the environment before they are detected, the more time they have to execute their attack."
VMDR helps you to prevent, identify and respond to the most critical threats promptly and proactively, reducing your time to remediate (TTR). -
Full visibility and control
VMDR gives you full clarity across your IT environment, and eliminates the blind spots that make it harder for you to identify the threats that you must address immediately. Visibility should be "horizontal" — all your hardware and software assets, known and unknown, wherever they reside and whatever their type. It should also be "vertical", offering a detailed, multidimensional view of each asset, including its IT and security data, so you can detect configuration, security and policy issues. -
Reduced risk
According to the Center for Internet Security (CIS), you can slash your cyber attack risk by 85% if you implement the first five of its 20 core CIS Controls and Resources:- Inventorying all your assets
- Ensuring they’re properly configured
- Continuously assessing their vulnerabilities Prioritizing remediation
- Controlling use of administrative privileges.
In other words, these core elements of VMDR will result in a whopping reduction in the probability of hacker intrusions, data breaches, malware infections, and violations of internal policies and government regulations.
The truth is that not every vulnerability is urgent – and even the urgent ones aren’t necessarily a top priority for every vulnerable system or application. To understand your exposire risk, you need the right context.
For example, 100 of your systems have a vulnerability rated "Critical" but the priority should be placed on the 11 systems that also contain sensitive data or critical business functions, and are connected to the public internet. "If you address just these 11 systems, though, you greatly reduce your attack surface and your exposure to risk. Having context enables you to prioritize effectively," a Qualys expert wrote in the Help Net Security article The Importance of Proactive Patch Management. -
Lower TCO and higher productivity
Organizations lose so much time, money and effort when infosec teams must use a plethora of point tools that provide a limited, fragmented view of the IT environment. A cloud-based, all-in-one VMDR solution provides end-to-end vulnerability management, detection and response, with a single pane of glass view and centralized control of your network’s security posture. That way, infosec pros can work smarter and faster, optimizing resources and reducing risk.

What are VMDR Best Practices
-
Don’t forget about misconfigurations
Scanning for vulnerabilities isn’t enough. A critical server can have all its vulnerabilities patched, but if its default admin password was never changed, it’s at a high risk of getting compromised. VMDR includes comprehensive assessment of misconfigurations, helping you boost asset security and compliance beyond open vulnerabilities. -
Centralize patch management
In a 2019 survey of 340 IT and infosec professionals done by the research firm Enterprise Strategy Group, 42% of respondents said they struggle with patching vulnerabilities in a timely manner. The same percentage of respondents reported difficulties tracking vulnerability and patch management processes, including vulnerability scanning, trouble ticketing, change management, patching and incident closure.
This friction in the process causes delays deploying patches, which in turn can lead to breaches. That’s why patch management should be part of an integrated breach-prevention program that includes asset inventory, vulnerability management and threat prioritization. "When patch management is isolated, time-to-remediation slows down," a Qualys expert wrote in the Black Hat article Boosting Patch Management Is Key For Breach Prevention.
VMDR centralizes, consolidates and automates the patch management process, making it uniform, coordinated and efficient. You go from manual to automated correlation of vulnerabilities and patches. You move away from having heterogeneous patching tools administered independently by multiple teams, which leads to slow, erratic and ineffective remediation. You no longer have to wait weeks for a scheduled report to know if patches were applied successfully and required actions completed. -
Reach for the clouds
To build security into hybrid IT environments, including DevOps pipelines, you need scalable, cloud-based VMDR that’s able to assess the security and compliance of your entire infrastructure, store and analyze all the data in a cloud platform, and present it in dynamic, consistent dashboards. Only with this VMDR cloud-based architecture can you obtain end-to-end inventorying, assessment, prioritization and remediation of assets everywhere — on premises, in public clouds, in IoT networks, in Operational Technology systems, in mobile devices and more. -
Use a variety of sensors
A VMDR solution with multiple types of sensors will ensure you collect inventory and threat data comprehensively. It should include:- Physical appliances that scan on premises
- Virtual appliances that scan private clouds and virtualized environments
- Cloud appliances that scan public cloud IaaS and PaaS instances
- Passive network sniffers that monitor network activity continuously
- Lightweight, all-purpose agents installed on IT assets for continuous monitoring

Qualys VMDR — All-in-One Vulnerability Management, Detection, and Response
Bringing the #1 Vulnerability Management solution to the next level
The Enterprise TruRisk Platform, combined with its powerful lightweight Cloud Agents, Virtual Scanners, and Network Analysis (passive scanning) capabilities bring together all four key elements of an effective vulnerability management program into a single app unified by powerful out-of-the-box orchestration workflows.
Qualys Vulnerability Management, Detection and Response enables organizations to automatically discover every asset in their environment, including unmanaged assets appearing on the network, inventory all hardware and software, and classify and tag critical assets. VMDR continuously assesses these assets for the latest vulnerabilities and applies the latest threat intel analysis to prioritize actively exploitable vulnerabilities.
Finally, VMDR automatically detects the latest superseding patch for the vulnerable asset and easily deploys it for remediation. By delivering all this in a single app workflow, VMDR automates the entire process and significantly accelerates an organization’s ability to respond to threats, thus preventing possible exploitation.
Learn more at https://www.qualys.com/vmdr
Try it for free at https://www.qualys.com/tryvmdr
See for yourself. Try Qualys VMDR for free.
Start your free trial today. No software to download or install. Email us or call us at 1 (800) 745-4355.