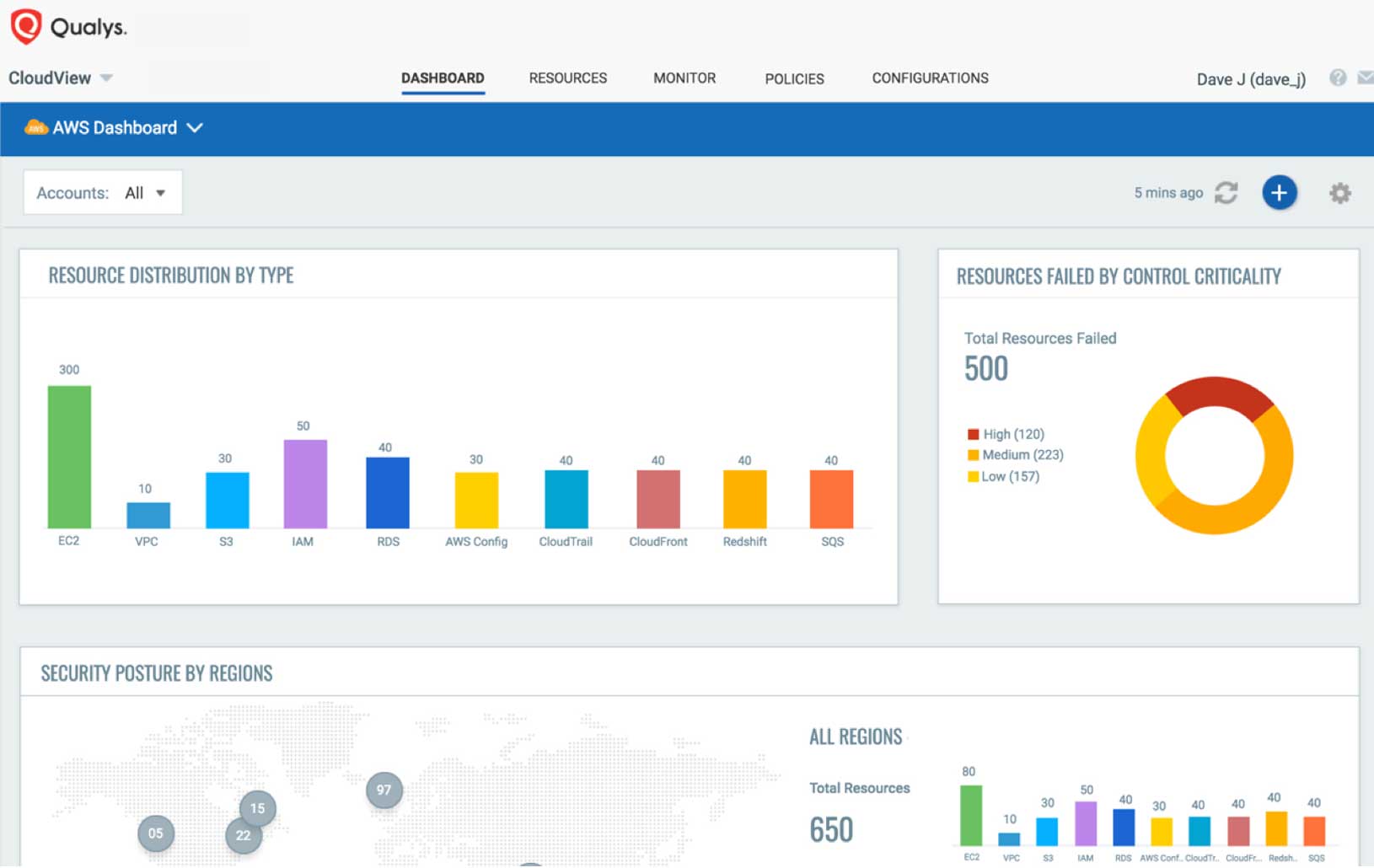
Public Cloud Integrations for Security and Compliance
Total visibility of your public cloud deployments.
Cloud computing platform providers operate on a “shared security responsibility” model, meaning you still must protect your workloads in the cloud. Qualys can help.
- Identify, classify, and monitor assets and vulnerabilities
- Comply with internal and external policies
- Prioritize vulnerability remediation
- Automatically find and eradicate malware infections on your websites
Security and compliance via native integrations
Qualys + AWS Highlights
Complete visibility, and end-to-end IT security and compliance of your AWS deployments and hybrid IT.
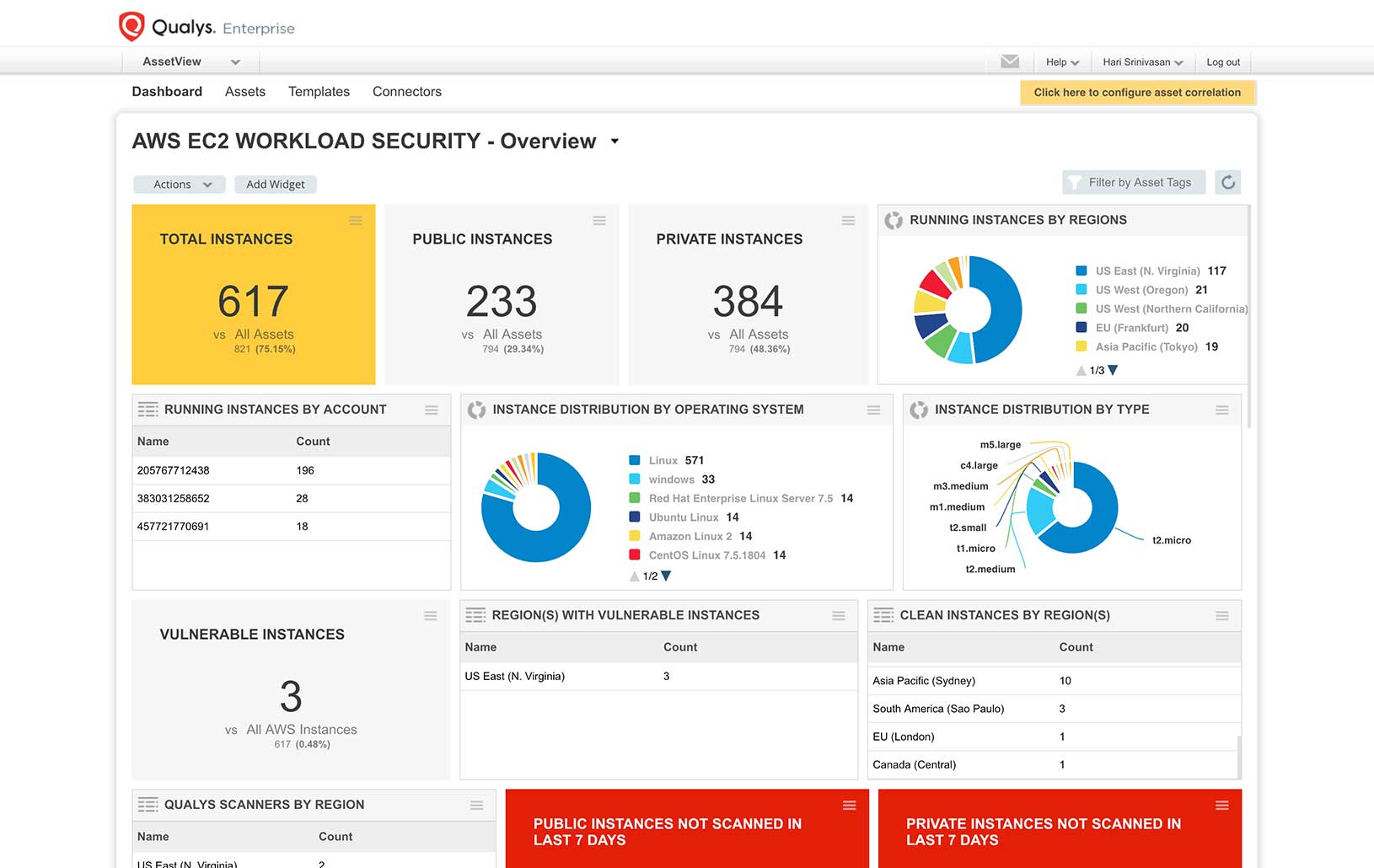
AWS workload security
Improve risk detection, prevention and response by performing a full set of security and compliance checks on your EC2 Instances, databases and web applications.
-
Vulnerability management
-
Policy compliance
-
File integrity monitoring
-
Indication of compromise
-
Web app scanning / firewall
-
Asset inventory and assessment
-
Other critical tasks

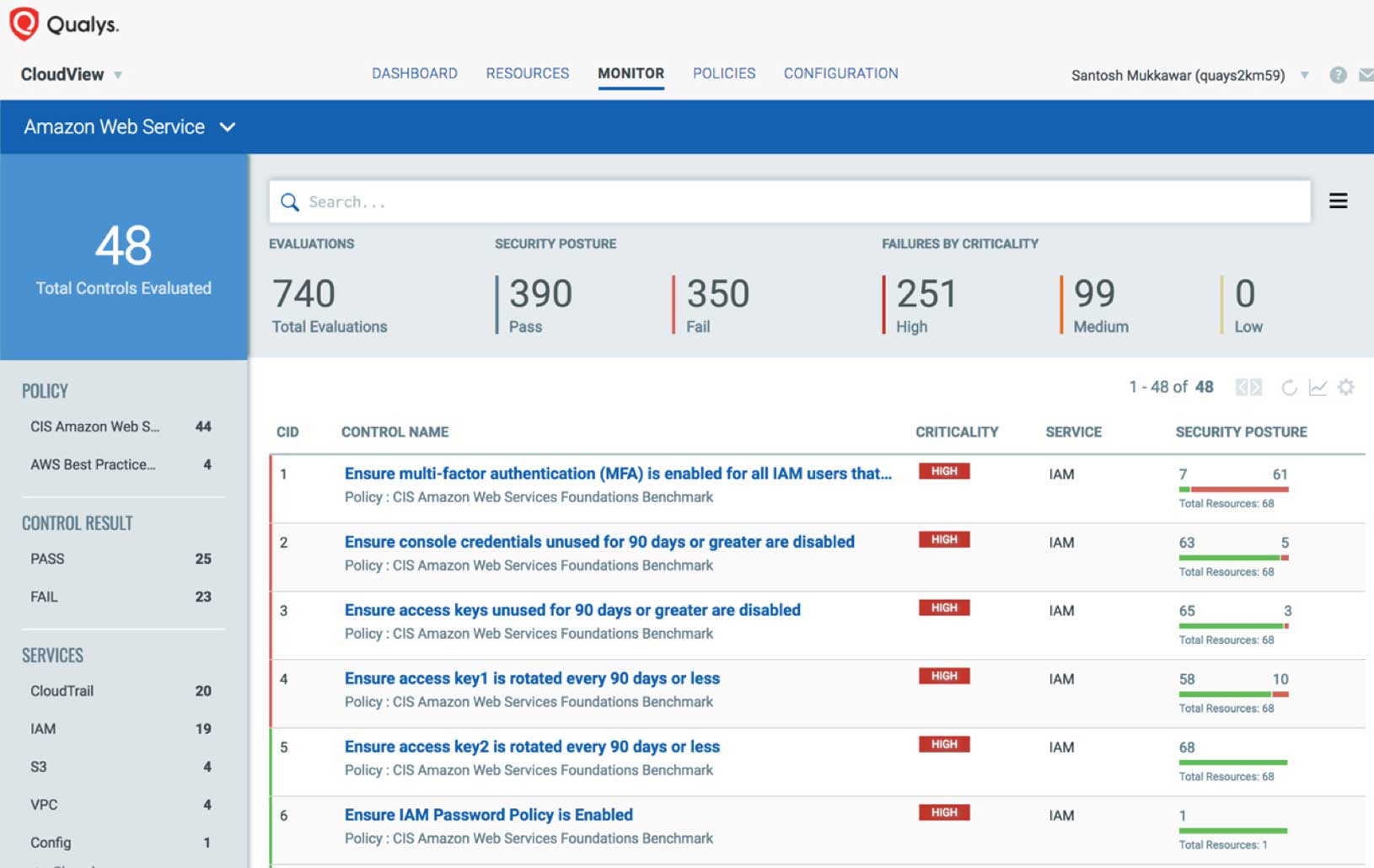
AWS infrastructure security
Monitor and assess your AWS environment against the CIS (Center for Internet Security) AWS Foundations Benchmark. Identify threats caused by misconfigurations, unauthorized access, and non-standard deployments. Get access to clear remediation recommendations so that you can maintain a solid security posture across your AWS resources like VPC, Security Groups, S3, IAM Users and RDS through automated, continuous assessments.

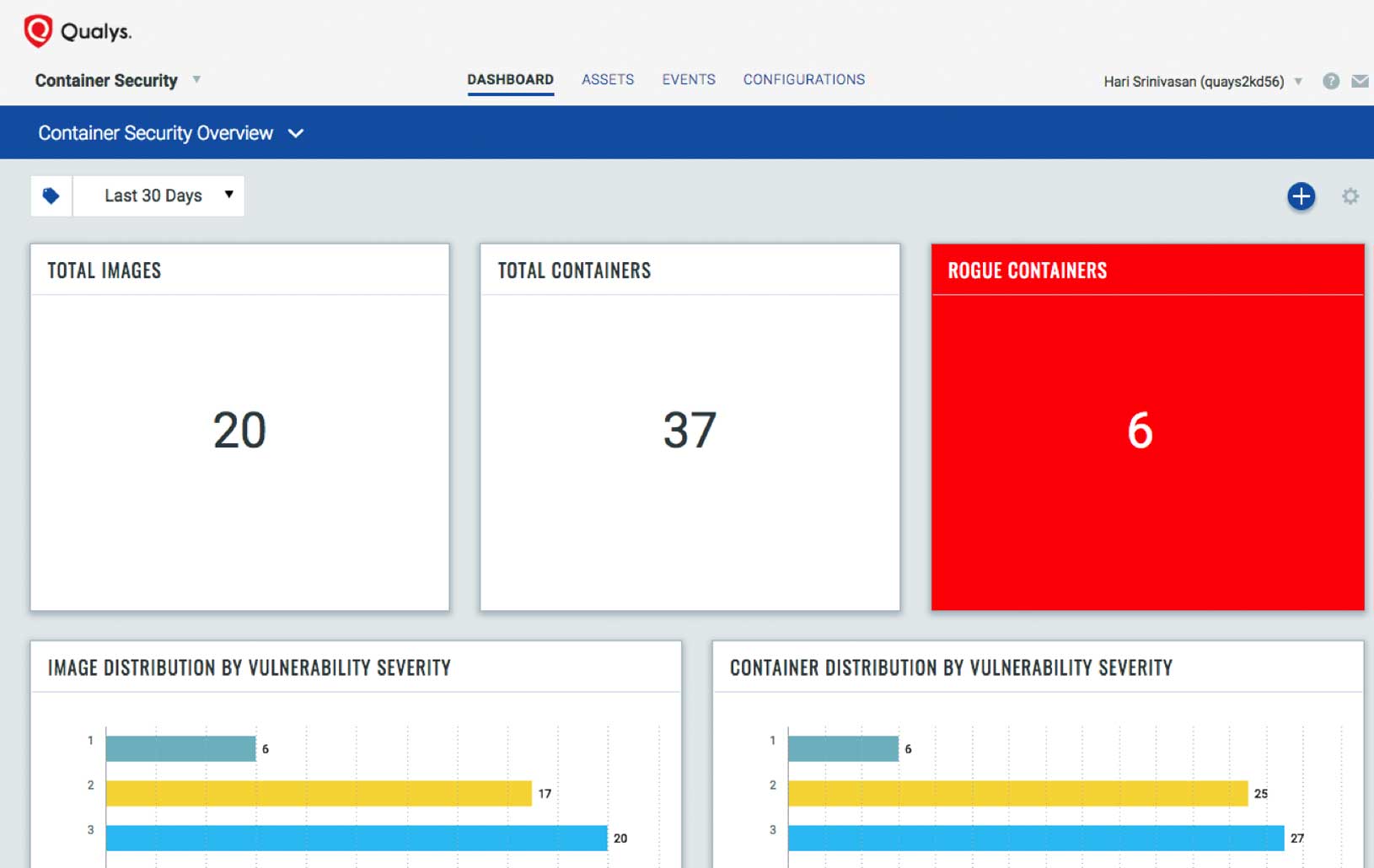
AWS container security
Qualys Container Security (CS) provides security coverage from the build to the deployment stages. Monitor and protect container-native applications on AWS without disrupting your existing Continuous Integration and Deployment (CI/CD) pipelines. Assess the contents of container images for vulnerabilities, control which images are deployed, gain visibility into runtime application activity, and also automatically enforce normal application behavior.
Qualys CS detects vulnerabilities and compliance issues with Docker images in the build pipeline and in AWS ECR, identifies behavioral anomalies and protects container runtimes deployed on AWS ECS, EKS and Fargate.

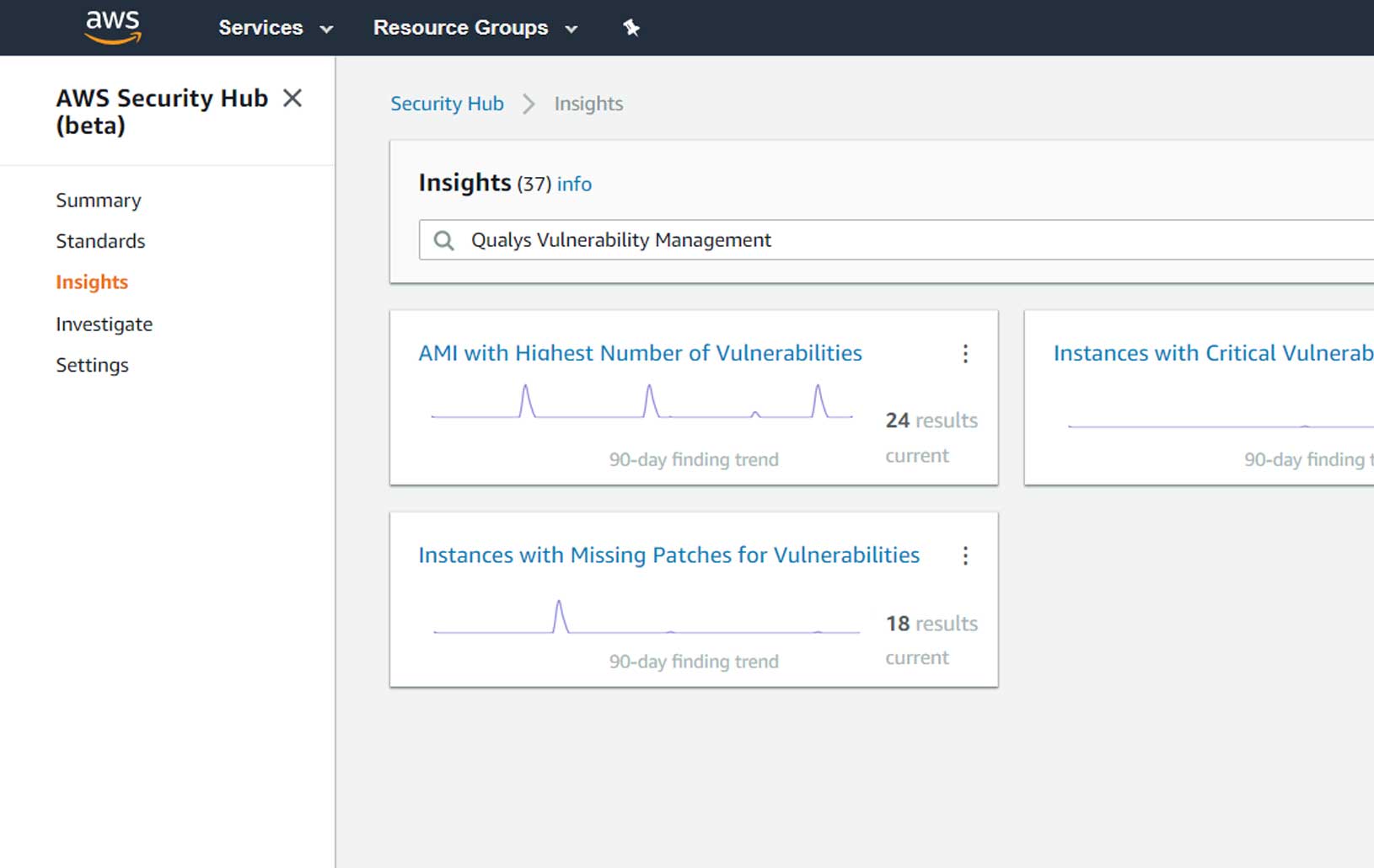
Native integration with AWS Security Hub
Natively integrate findings from the Qualys Vulnerability Management, Policy Compliance and Cloud Security Assessment apps into AWS Security Hub. Get real-time visibility into your security and compliance posture directly in the AWS console. Benefit from insights gained from the correlation of Qualys information with other data in AWS Security Hub to enable faster detection and prioritization of risks in AWS environments, enabling rapid automated remediation actions.
Learn more

DevOps security in AWS
Enterprise TruRisk Platform, with its robust APIs and native integrations with key DevOps tools, lets you build security into every function in the CI/CD tool chain. This allows developers and ops staff to do security checks, and enables security teams to provide support at the pace of DevOps. Qualys Cloud Agents can be easily embedded into the AMIs or installed on instances. This gives you an ideal way to integrate security at the source and provide complete visibility for elastic cloud workloads. Learn how our customers have implemented secure DevOps, and how you can do it as well.
Graviton ready
The Graviton Ready Qualys Cloud Agent provides customers cost savings on AWS’s Graviton2 ARM architecture while leveraging Qualys’ innovative Cloud Platform to protect their critical assets with integrated IT, compliance, and security. The Qualys Cloud Agent enables instant, global visibility of IT assets – with up-to-date asset configuration data for security, compliance, and response.

How we secure AWS
Enterprise TruRisk Platform sensors are always on, giving you continuous 2-second visibility of all your AWS assets. Remotely deployable, centrally managed and self-updating, the sensors come as physical or virtual appliances, or lightweight agents. Qualys Container Security and Web Application Firewall complement the sensors.
AWS Connector
Sync AWS EC2 instances, resources and their associated metadata
Virtual Scanners
Remotely scan instances across VPCs and Regions with pre-authorized scanners
Internet Scanners
Perform fast and efficient external scans
 Learn more about Qualys TotalCloud
Learn more about Qualys TotalCloud
Qualys + Azure Highlights
Complete visibility, and end-to-end IT security and compliance of your hybrid Azure deployments across Azure and Azure Stack.
Obtain visibility of your Azure deployments
Gain visibility, security and continuous compliance across your Azure public cloud, Azure Stack private cloud and hybrid infrastructure and workloads from a single-pane interface. Using the same Enterprise TruRisk Platform apps, sensors and analysis engine for both Azure and Azure Stack yields benefits such as:
-
360-degree view of all Azure assets from a centralized UI
-
Lower cost
-
Ease of use
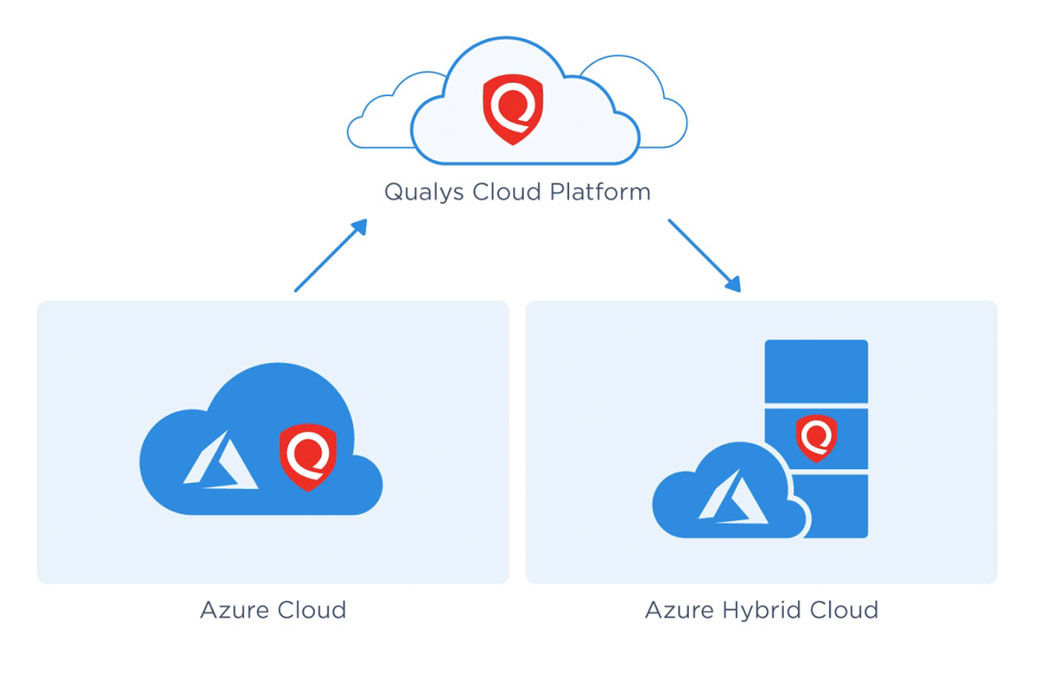
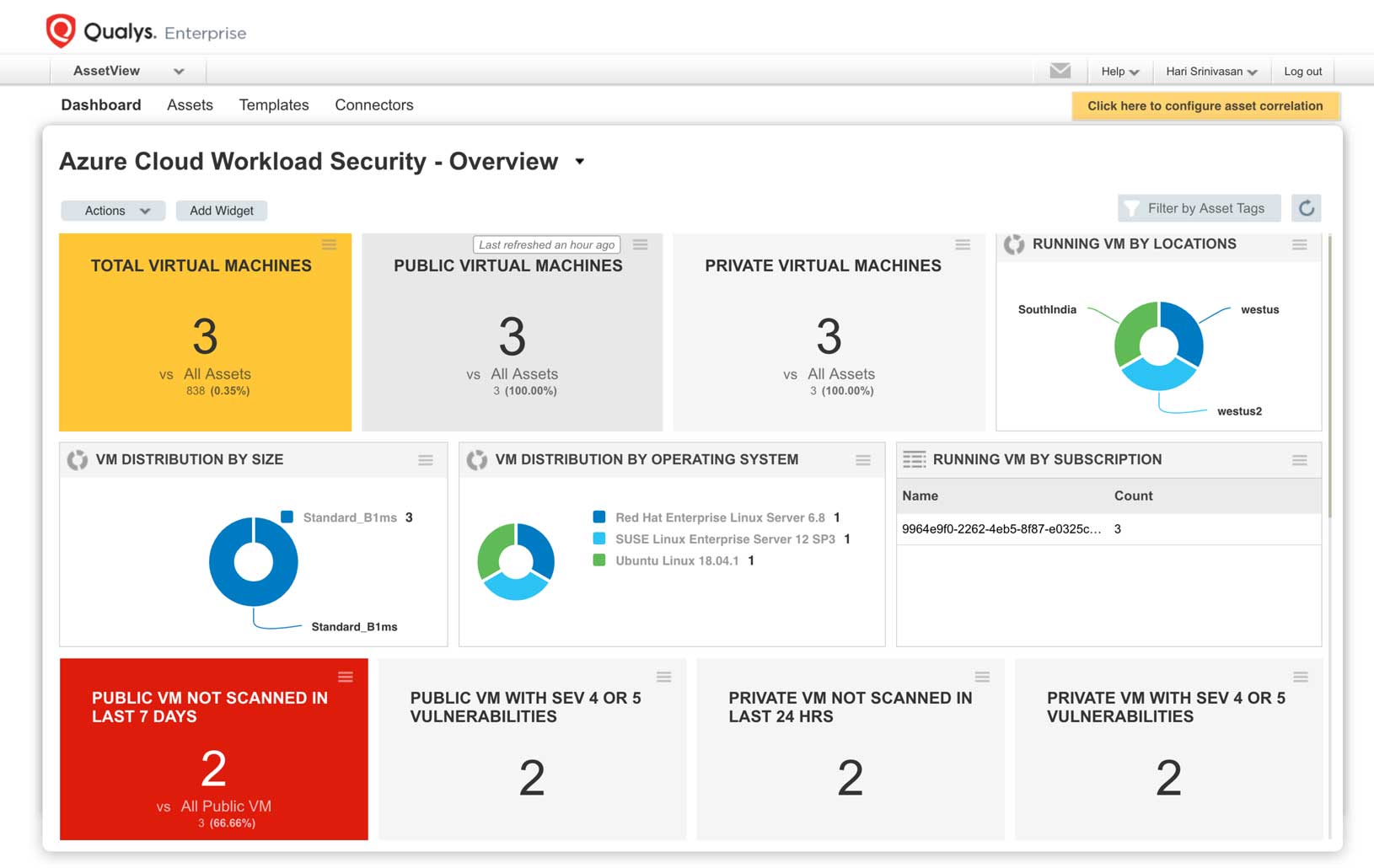
Secure workloads in Azure
Improve risk detection, prevention and response by performing a full set of security and compliance checks on your Azure virtual machines, databases and web applications.
-
Vulnerability management
-
Policy compliance
-
File integrity monitoring
-
Endpoint Detection & Response
-
Web app scanning / firewall
-
Other critical tasks

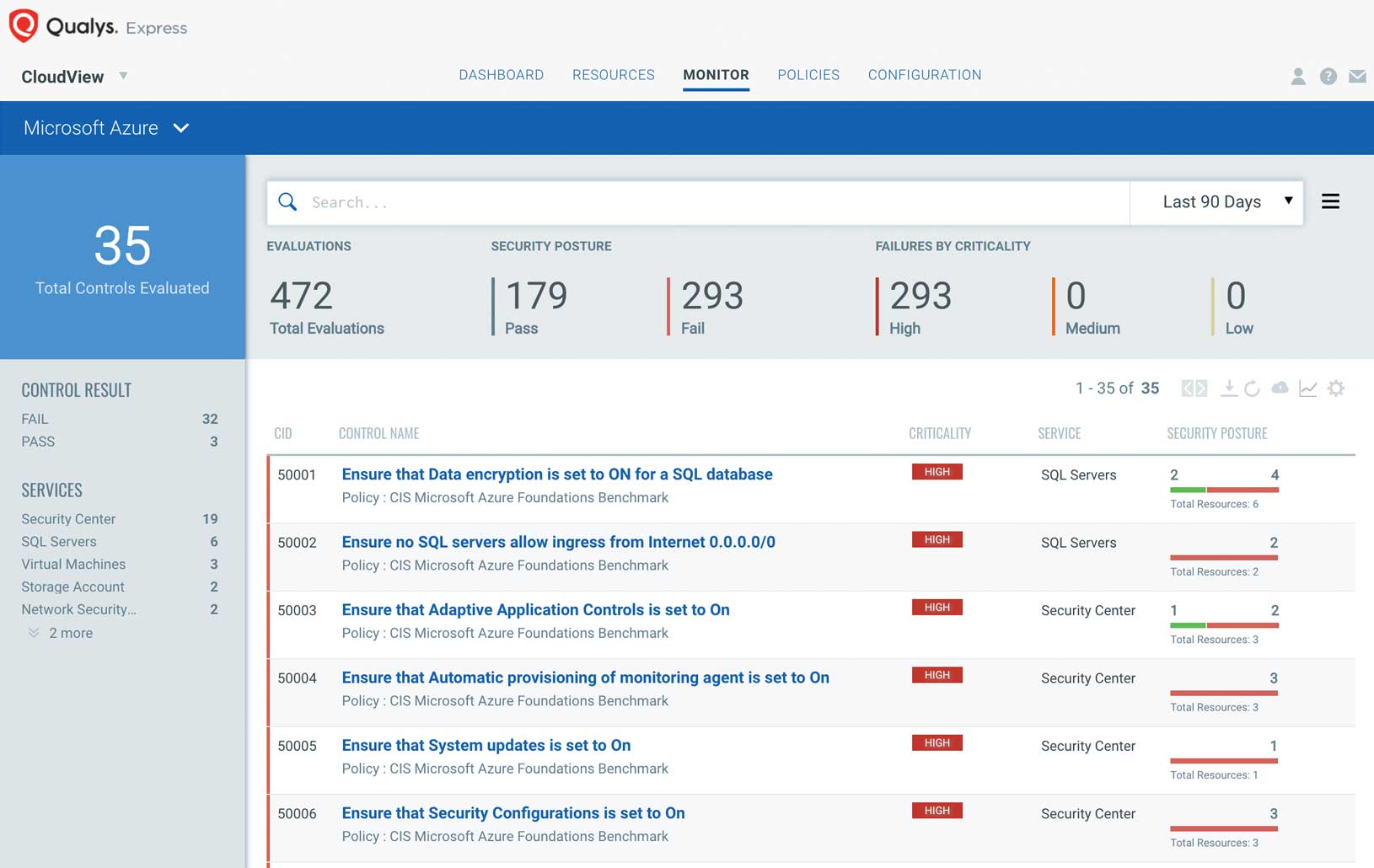
Assess Azure infrastructure security configuration
Monitor and assess your Azure environment against the CIS (Center for Internet Security) Microsoft Azure Foundations Benchmark. Identify threats caused by misconfigurations, unauthorized access, and non-standard deployments. Through automated, continuous assessments and clear remediation recommendations, you can maintain a solid security posture across your Azure resources like Virtual Networks, Network Security Groups, SQL Servers, and Storage Blobs.
Learn more


Secure container deployments
Qualys Container Security (CS) provides security coverage from the build to the deployment stages. It lets you monitor and protect container-native applications on Azure without disrupting your existing Continuous Integration and Deployment (CI/CD) pipelines. With Qualys CS, you can assess the contents of container images for vulnerabilities, control which images are deployed, gain visibility into runtime application activity, and also automatically enforce normal application behavior.
Qualys CS detects vulnerabilities and compliance issues with Docker images in the build pipeline and in Azure Container Registry, identifies behavioral anomalies and protects container runtimes deployed on AKS and Azure Container Instances.
Learn more

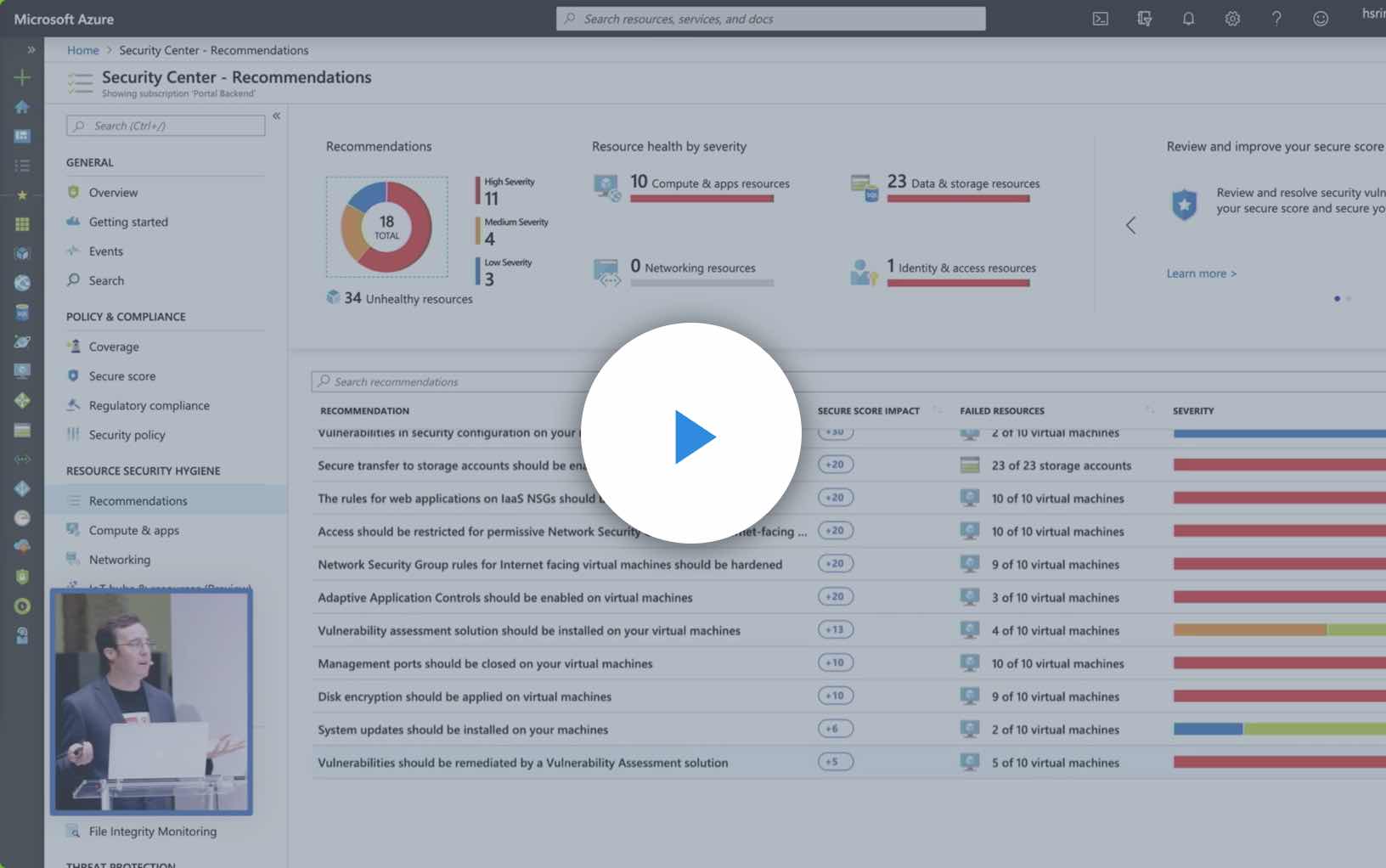
Integrate with Azure Security Center
Azure Security Center – a unified security management and monitoring console – now detects Azure virtual machines and automatically deploys the lightweight Qualys Cloud Agents on them. The agents gather vulnerability data and send it to the Enterprise TruRisk Platform, which in turn provides vulnerability and system health monitoring data back to Azure Security Center.
DEMO: Security built in Azure – not bolted on (02:59)
VIDEO: Integrating Qualys with Microsoft Azure Security Center (04:54)

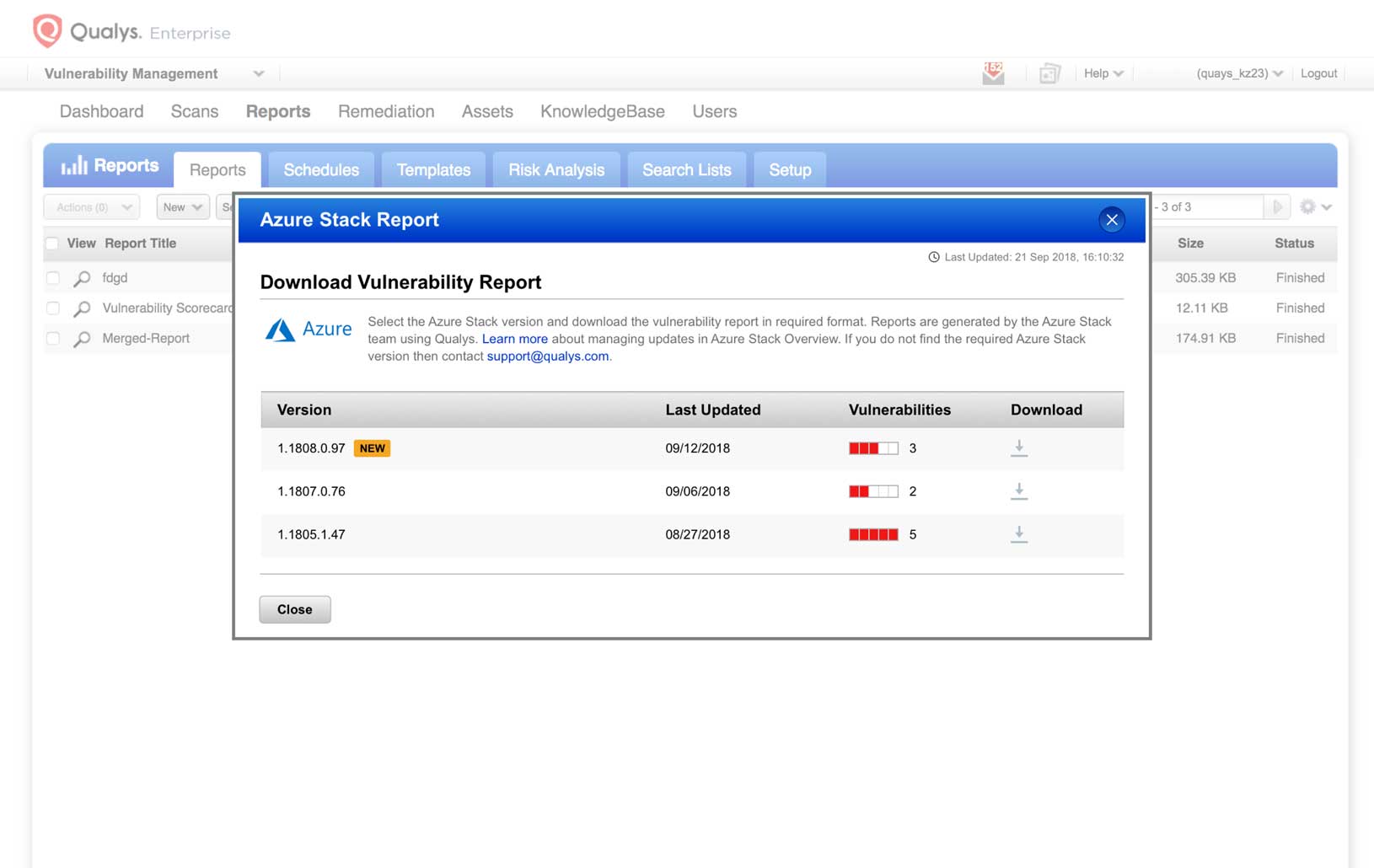
Secure Azure Stack infrastructure and workloads
Qualys assesses the security and compliance posture of Azure Stack, the version of Azure designed for on-premises deployments. You can either deploy Qualys Virtual Scanner Appliances or Qualys Cloud Agents to assess Azure Stack’s control plane infrastructure and workloads.
Learn more

How we secure Azure
We use Enterprise TruRisk Platform sensors, which are always on, giving you continuous 2-second visibility of all your Azure assets. Remotely deployable, centrally managed and self-updating, the sensors come as physical or virtual appliances, or lightweight agents. Qualys Container Security and Web Application Firewall complement the sensors.
Azure Connector
Know what you have in the cloud. Sync Azure virtual machines, resources and their associated metadata information
Virtual Scanners
Remotely scan instances across virtual networks and regions with network scanners. Click and deploy scanners directly from the marketplace
Cloud Agents
Collect data in real time with our lightweight agent. Pre-deploy into the image or deploy on the VMs after their creation
Learn moreInternet Scanners
Gain a hacker’s perspective with fast and efficient external scans of public facing virtual machines and load balancers
 Learn more about Qualys TotalCloud
Learn more about Qualys TotalCloud
Qualys + GCP Highlights
Complete visibility, and end-to-end IT security and compliance of your GCP deployments.
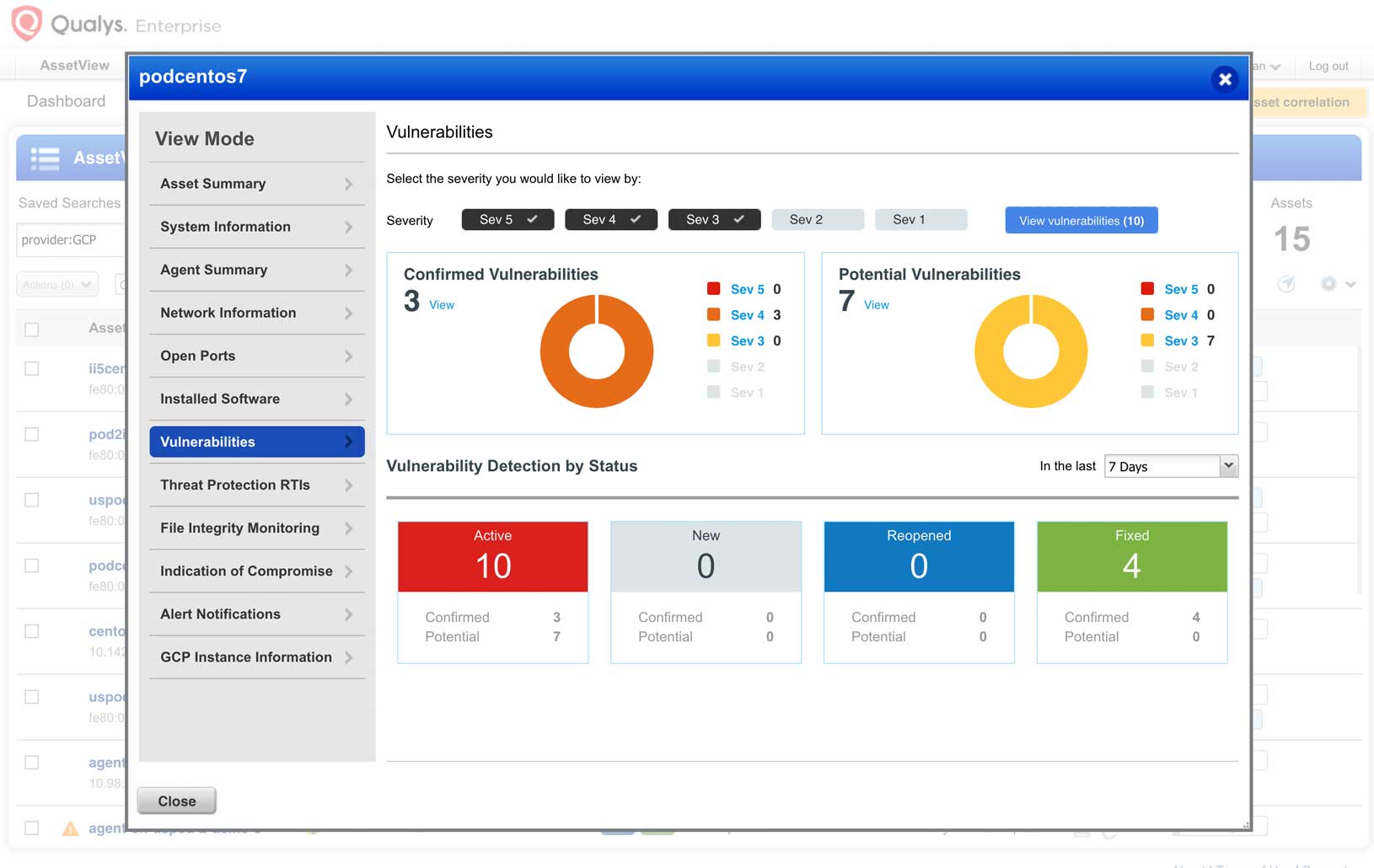
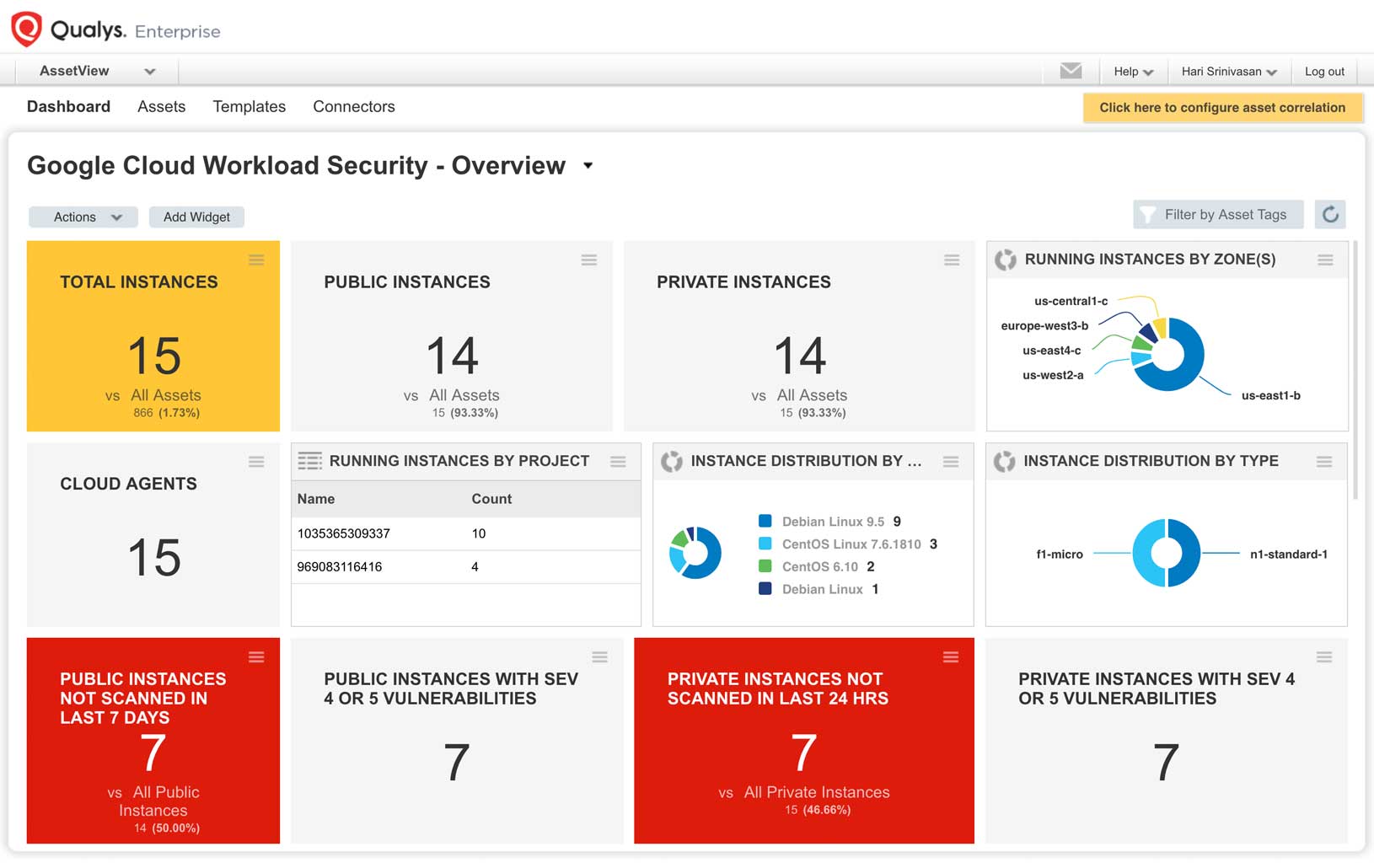
Google Cloud workload security
Improve risk detection, prevention and response by performing a full set of security and compliance checks on your GCP compute instances, databases and web applications.
-
Vulnerability management
-
Policy compliance
-
File integrity monitoring
-
Indication of compromise
-
Web app scanning / firewall
-
Other critical tasks

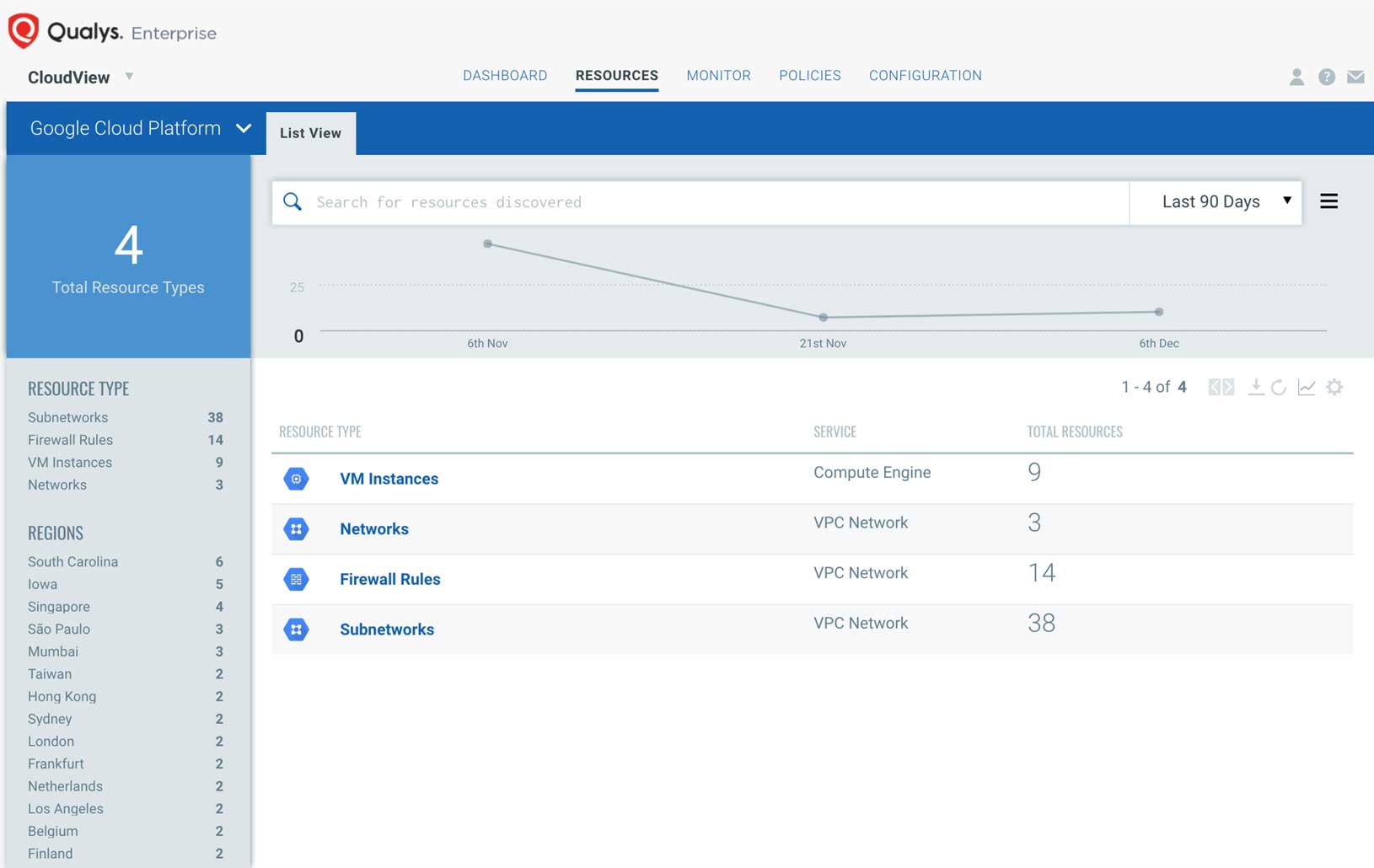
Google Cloud infrastructure security
Gain visibility into your GCP projects, and know about the assets like Virtual Machines, Networks, Firewall Rules, Subnetworks and their relationships. Monitor and assess your GCP environment against the CIS (Center for Internet Security) Google Cloud Platform Foundations Benchmark. Identify threats caused by misconfigurations, unauthorized access, and non-standard deployments.
(Beta Coming Soon)


GCP container security
Qualys Container Security (CS) provides security coverage from the build to the deployment stages. Monitor and protect container-native applications on GCP without disrupting your existing Continuous Integration and Deployment (CI/CD) pipelines. Assess the contents of container images for vulnerabilities, control which images are deployed, gain visibility into runtime application activity, and also automatically enforce normal application behavior.
Qualys CS detects vulnerabilities and compliance issues with Docker images in the build pipeline and in Google container registry, identifies behavioral anomalies and protects container runtime deployed on Google Kubernetes Engine.

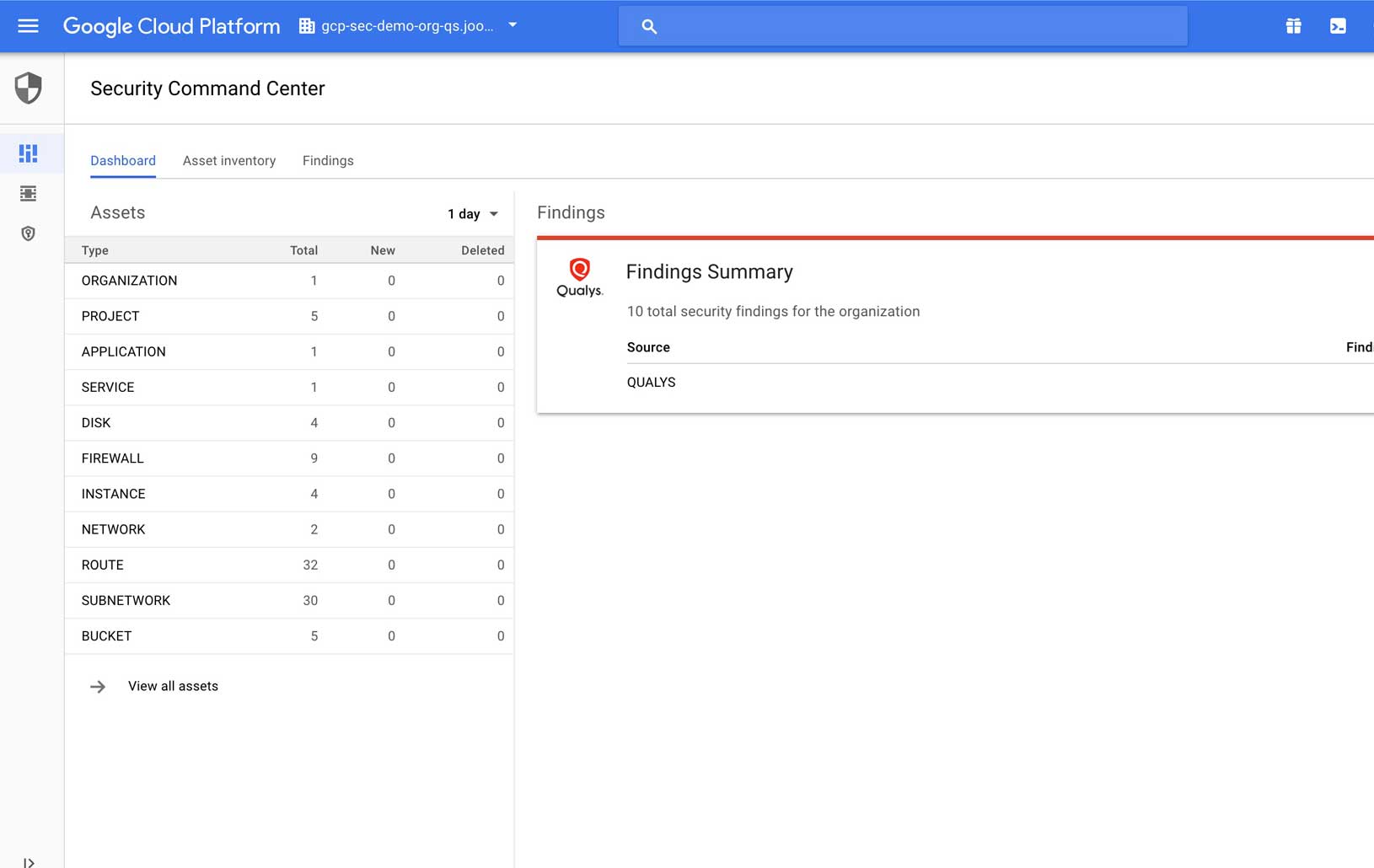
Native integration with Google Cloud Security Command Center
Natively integrate findings from the Qualys Vulnerability Management and Policy Compliance apps into Google Cloud Security Command Center. Get real-time visibility into your security and compliance posture directly in the GCP console. Benefit from insights gained from the correlation of Qualys information with other data in Google Cloud Security Command Center to enable faster detection and prioritization of risks in GCP environments.
Learn more

How we secure GCP
We use Enterprise TruRisk Platform sensors, which are always on, giving you continuous 2-second visibility of all your GCP assets. Remotely deployable, centrally managed and self-updating, the sensors come as physical or virtual appliances, or lightweight agents. Qualys Container Security and Web Application Firewall complement the sensors.
Virtual Scanners
Remotely scan instances across virtual networks and regions with network scanners. Click and deploy scanners directly from the marketplace
Cloud Agents
Collect data in real time with our lightweight agent. Pre-deploy into the image or deploy on the VMs after their creation
Learn moreInternet Scanners
Gain a hacker’s perspective with fast and efficient external scans of public facing virtual machines and load balancers
 Learn more about Qualys TotalCloud
Learn more about Qualys TotalCloud
Qualys + Oracle Cloud Infrastructure (OCI) Highlights
Enhanced vulnerability management across your OCI environment
Gain enhanced vulnerability management across your Oracle Cloud Infrastructure environment
Native integration between Qualys Cloud Agent technology and OCI provides continuous Qualys Vulnerability Assessment services for OCI Compute Instances from within OCI’s Vulnerability Scanning Service (VSS).
-
Hybrid/Multi-cloud findings available in Enterprise TruRisk Platform
-
OCI Compute Instance findings available in OCI VSS/Cloud Guard
-
Vulnerability reporting available via the Enterprise TruRisk Platform and in OCI Cloud Guard
-
Qualys also captures OCI metadata

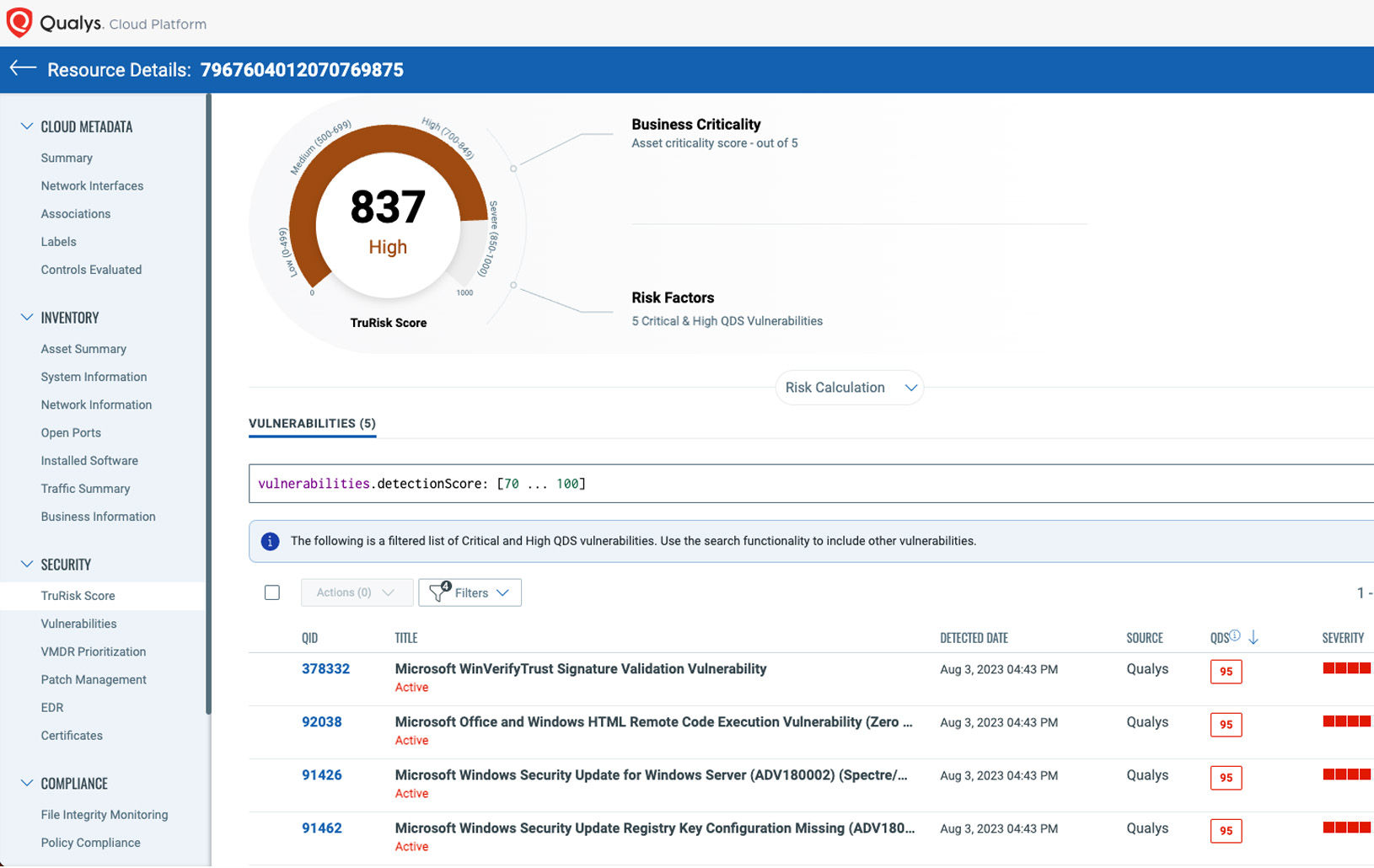
Oracle Cloud workload security
Improve risk detection, prevention and response by performing a full set of security and compliance checks on your OCI compute instances, databases and web applications.
-
Vulnerability management
-
Policy compliance
-
File integrity monitoring
-
Indication of compromise
-
Web app scanning / firewall
-
Other critical tasks

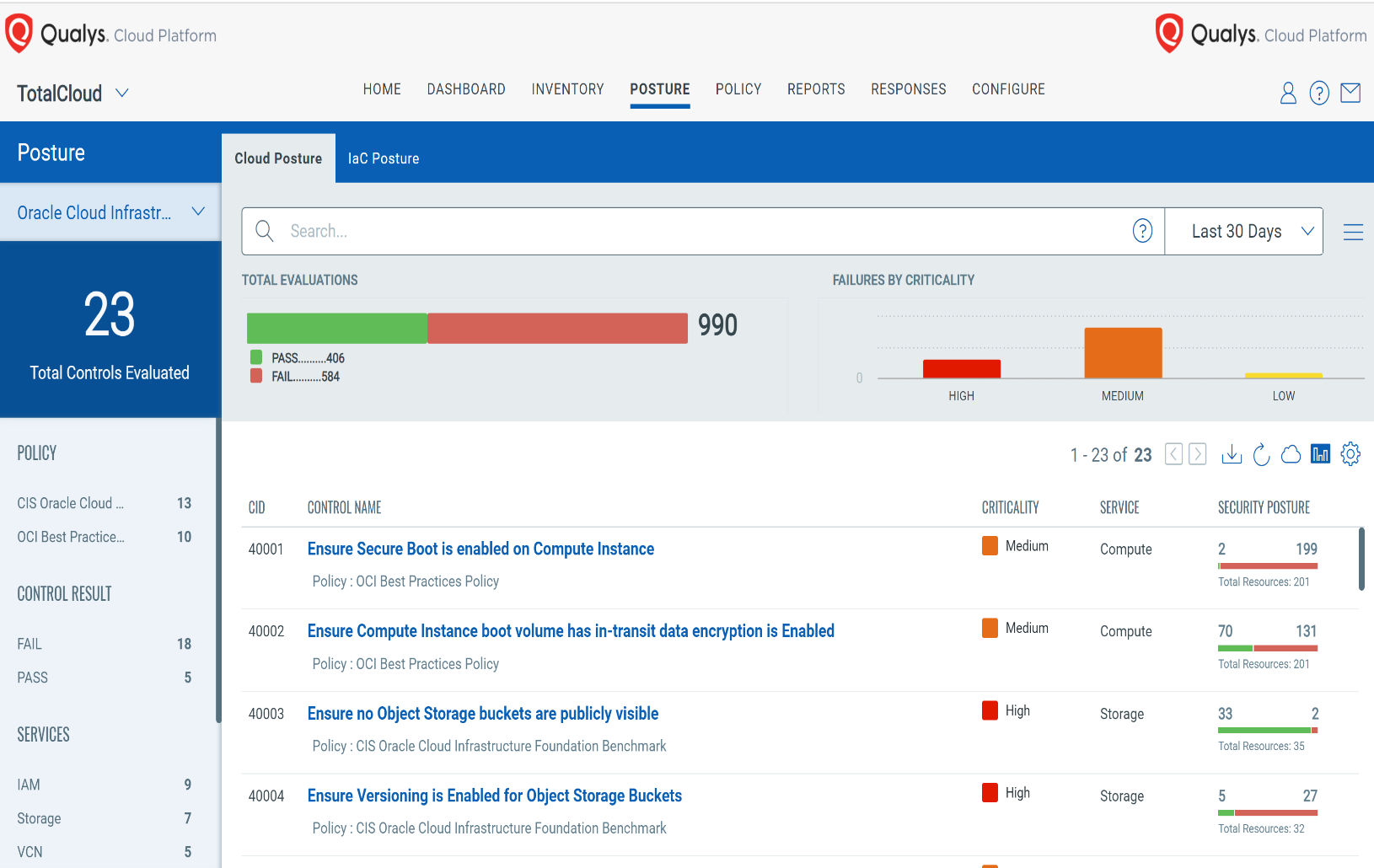
Oracle Cloud Infrastructure security
Gain visibility into your OCI Tenancy, and know about the assets like Compute Instances, Networks, Firewall Rules, Subnetworks and their relationships. Monitor and assess your OCI environment against the CIS (Center for Internet Security) Oracle Cloud Platform Foundations Benchmark. Identify threats caused by misconfigurations, unauthorized access, and non-standard deployments.

Native integration with Oracle Cloud Security Command Center
Qualys has integrated with the OCI Vulnerability Scanning Service (VSS). By using Qualys’ platform to defend hybrid IT environments, you gain a unified view of your security posture and can apply the same standards and processes on-premises and in the cloud. This can help you reduce your total cost of ownership (TCO) and view all data in one place. When a major attack like Log4j is unleashed, you can quickly assess your risk by running vulnerability scans across your entire environment, understand the extent of your exposure, and act from a single console instead of assembling fragmented information from siloed tools. You can now natively integrate findings from Qualys Vulnerability Management and Policy Compliance apps into OCI and have real-time visibility into your security and compliance posture directly in the OCI console.
How we extend Oracle Cloud
We use Enterprise TruRisk Platform sensors, which are always on, giving you continuous 2-second visibility of all your OCI assets. Remotely deployable, centrally managed and self-updating, the sensors come as physical or virtual appliances, or lightweight agents. Qualys Container Security and Web Application Firewall complement the sensors.
Virtual Scanners
Remotely scan instances across virtual networks and regions with network scanners. Click and deploy scanners directly from the marketplace
Cloud Agents
Collect data in real time with our lightweight agent. Pre-deploy into the image or deploy on the VMs after their creation
Learn moreInternet Scanners
Gain a hacker’s perspective with fast and efficient external scans of public facing virtual machines and load balancers
 Learn more about Qualys TotalCloud
Learn more about Qualys TotalCloud