Industry-leading cloud service for scalable, simple and powerful protection of web applications
![JIVE]()
We are excited that Qualys WAF will allow us to act quickly and respond to threats by using the one-click virtual patching feature to remediate active vulnerabilities.
David Cook Chief Security Officer at Jive Software
Qualys WAF Highlights
Prevent breaches by blocking
attacks on web server
vulnerabilities
You can’t protect – nor defend yourself from – what you don’t know is in your network, like unapproved devices and unauthorized software. Qualys gives you full horizontal visibility of all hardware and software, scaling up to millions of assets – on premises, in cloud instances and mobile endpoints.
-
Protect cloud apps
- Quickly and easily protect apps in public or private clouds by deploying Qualys Virtual Firewall Appliances alongside your web apps. No need to buy nor maintain special hardware
- Add as many applications as necessary as often as you need, as these virtual machines scale seamlessly.
- Ensure high performance and availability of business-critical web apps thanks to built-in load balancing and application monitoring.
- Enforce applications’ SSL/TLS layer thanks to Qualys WAF’s offloading capability
-
Adopt a new approach for web app security with Qualys WAF’s adaptive policies, which are always up to date and don’t require specialized expertise, nor complex rulesets to configure and maintain
- Describe the security level for each application with a few clicks, and Qualys WAF automatically decides what to do in different situations
- Simplify Qualys WAF configuration with Qualys generic templates, or with built-in security policies for popular platforms such as WordPress, Joomla, Drupal and Outlook Web Application, Sharepoint
-
Defend yourself from current and future threats with customizable protection
- Block a wide range of attacks such as Cross-Site Scripting (XSS), SQL injection, Remote Command Execution, XXE and more with native protection. As new threats emerge, Qualys’ security experts update Qualys WAF’s rules, which are then downloaded and spotted by the proprietary detection engine.
- Tailor how Qualys WAF handles different types of threats, from simply logging the event to actively blocking it.
- Create custom security rules to address specific security needs of your application and reduce the attack surface.
- Maintain website uptime by complementing network DDoS defenses with controls over applications’ latency.
- Protect your users against clickjacking, Cross-Site Scripting (XSS), and other browser-based attacks with Qualys WAF’s security features for modern web browsers
- Integrate Qualys WAF API into your DevOps environment and protect web servers hosting the apps you’re rapidly and iteratively developing and deploying
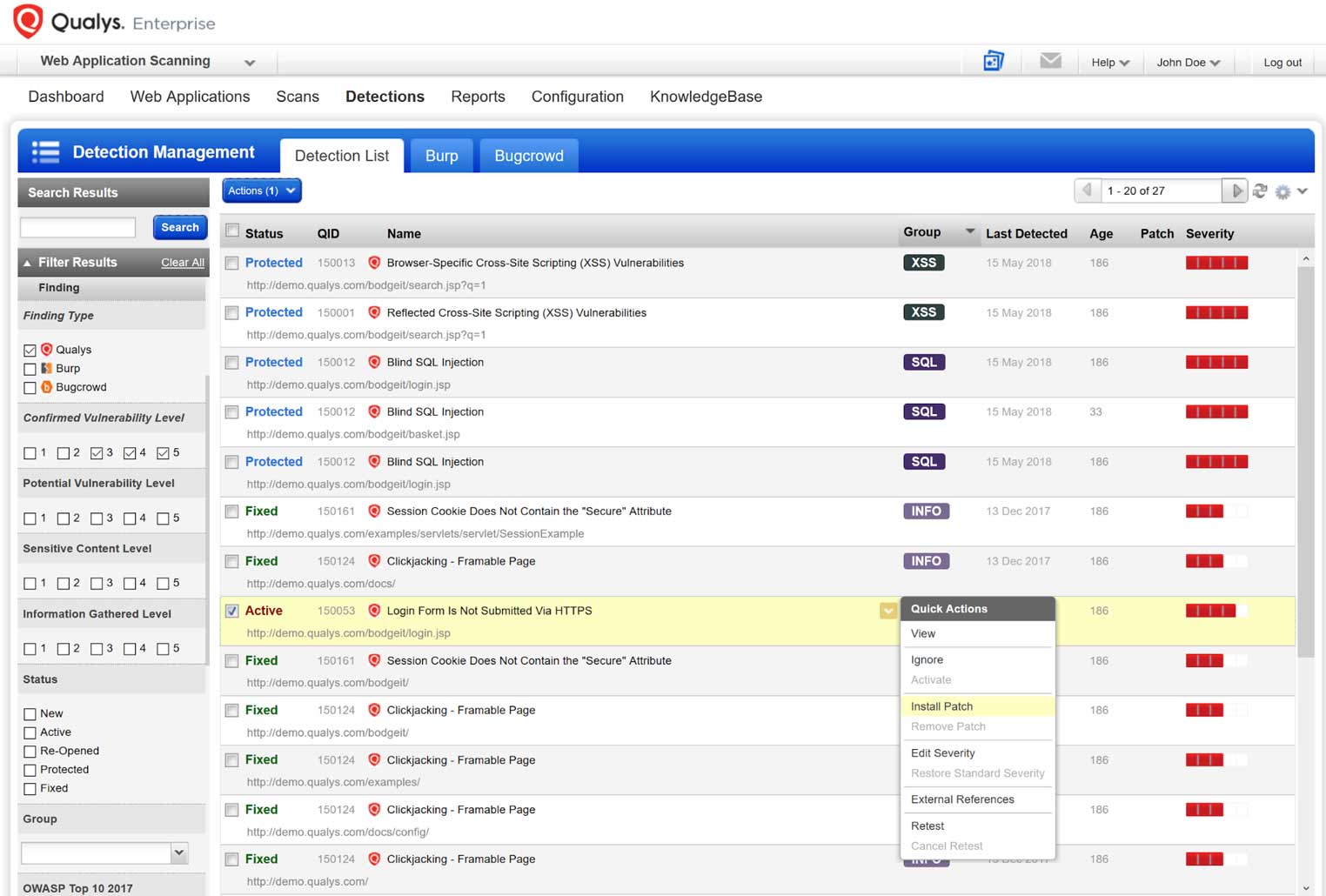
Benefit from native, deep integration between Qualys WAF and Qualys WAS
Empower security professionals to rapidly discover and mitigate critical security concerns. With the new ScanTrust feature, Qualys WAF combines with Qualys WAS to provide true visibility for your web applications: Detect with Qualys WAS, protect with Qualys WAF and get scalable scanning, false-positive reduction and one-click patching to web apps.
-
From a single console, use Qualys WAS to detect vulnerabilities in web apps, including mobile and IoT apps, and – with one click – mitigate them with Qualys WAF virtual patches
-
Leverage the creation of these virtual patch rules to fine-tune policies, remove false positives, and customize security rules
-
Avoid the redundancies and gaps that come with trying to glue separate, siloed solutions. Reduce operating costs by reducing staff
-
Evaluate and create exceptions to web events to better prioritize and mitigate vulnerabilities by combining Qualys WAF rules and policies with Qualys WAS scan data
-
Integrate web app scan data via a rich, extensive set of APIs into other security and compliance systems, such as firewalls, and SIEM and ERM solutions

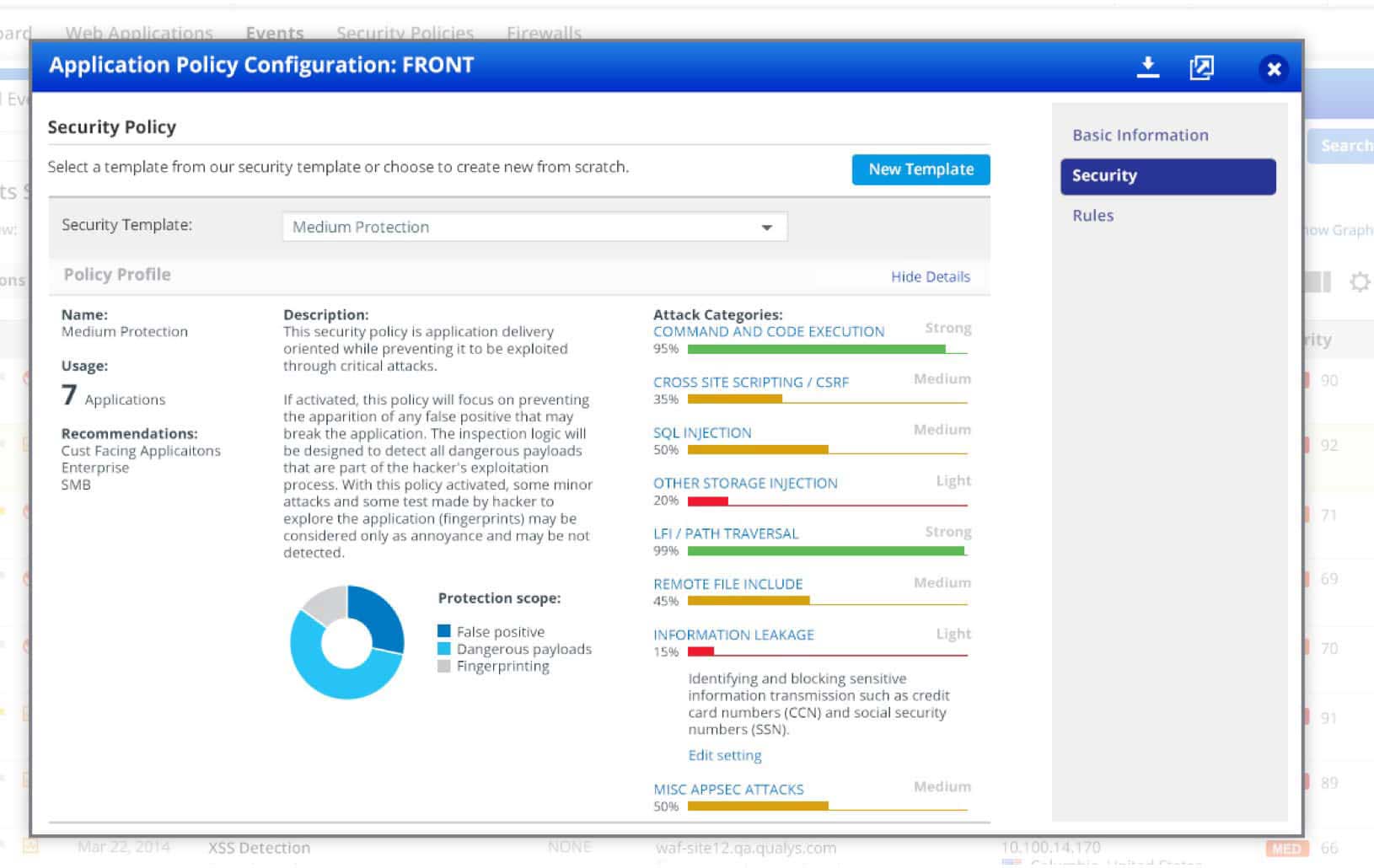
Simplify IT compliance
It’s easier than ever for employees to bypass their IT department and adopt web apps, a trend that generates significant security and compliance risks. Simultaneously, the quantity and complexity of government regulations, industry mandates and internal policies that impact InfoSec technologies and processes continues to grow. Qualys WAF can help you comply.
-
Address mandates such as PCI DSS 6.6 that require app firewalls
-
Comply with policies and regulations that prohibit access to certain web applications or information from particular locations by restricting access from specific countries or network address blocks
-
Prevent transmission of sensitive data by blocking users’ ability to upload or download content or files in unapproved or suspicious formats

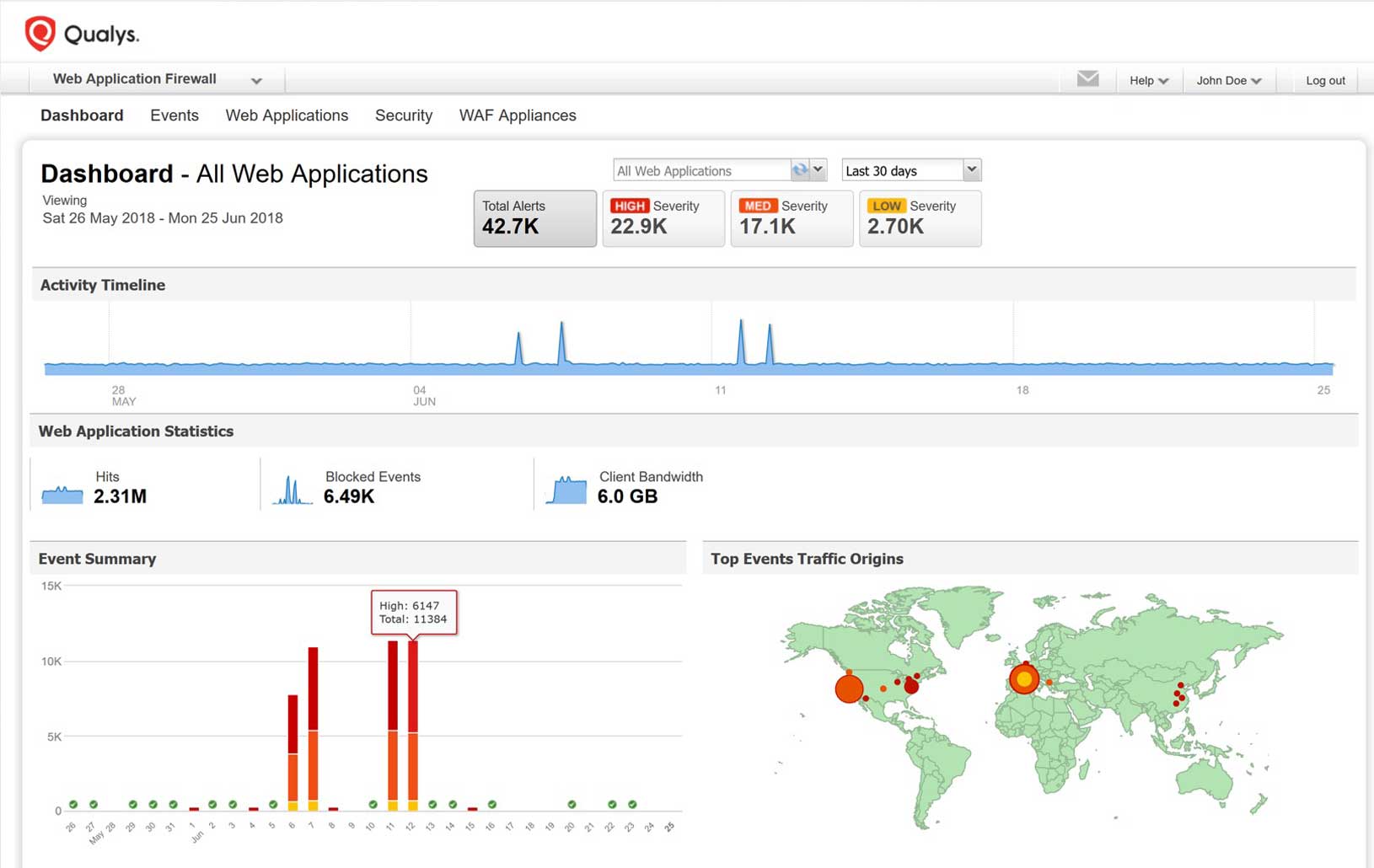
Visualize and report
You need an easy, intuitive way of understanding the security of all your web applications at once. Qualys WAF gives your security team complete visibility into its data for continuous monitoring, risk assessments and remediation paths. Qualys WAF tools for visualization and reporting include a graphics-rich dashboard, interactive insights and detailed information on each threat and ways to address it.
-
Spot unusual patterns in the dashboard, which shows summarized website traffic information and trends of Qualys WAF security events, including when they occurred and where they originated
-
Quickly assess severity and adjust your security settings for aggressive mitigation or to minimize false positives by leveraging detailed information on each threat detected by Qualys WAF
-
Use extensive filtering and dynamic search capabilities to identify suspicious activity, drill down into threat data and the Qualys KnowledgeBase, and gain actionable insights into the threat landscape

See for yourself. Try Qualys for free.
Start your free trial today. No software to download or install. Email us or call us at 1 (800) 745-4355.

