Vulnerability Management, Detection & Response
De-risk your business with the world's #1 vulnerability management solution.
The industry standard for risk-based vulnerability management.
Measure Risk
with 25+ sources of Real-Time Threat Intelligence (RTI) using TruRisk™.
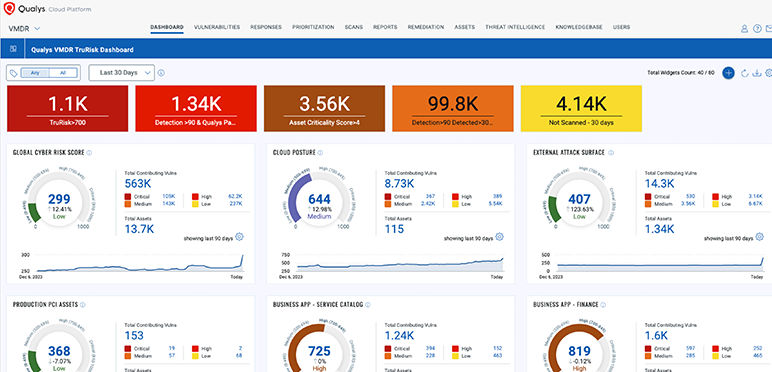
Accurately measure, quantify, and track risk reduction over time, across vulnerabilities, assets, and business units.
Communicate Risk
By routing vulnerabilities to the right owners, driving focus on critical business risk.
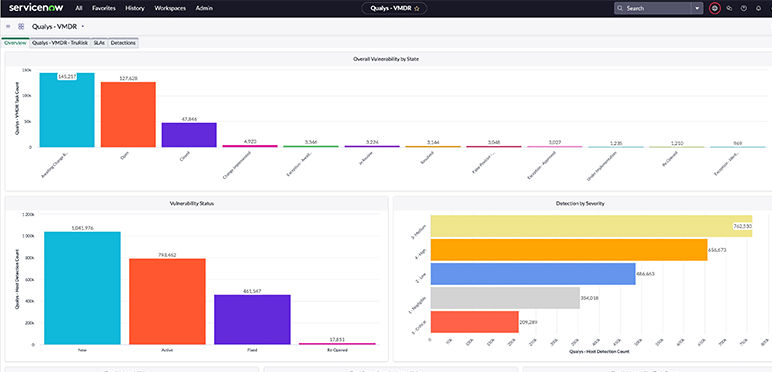
Communicate risk precisely across different teams, business units and geographic locations by leveraging dashboards, reports and ITSM tools.
Eliminate Risk
60% faster with built-in patching and remediation workflows.
Patch any device anywhere, leverage multiple avenues from remediation to mitigation and block attack paths to eliminate risk.
Qualys Enterprise TruRisk™ Platform
Reduce Cybersecurity Risk Effectively
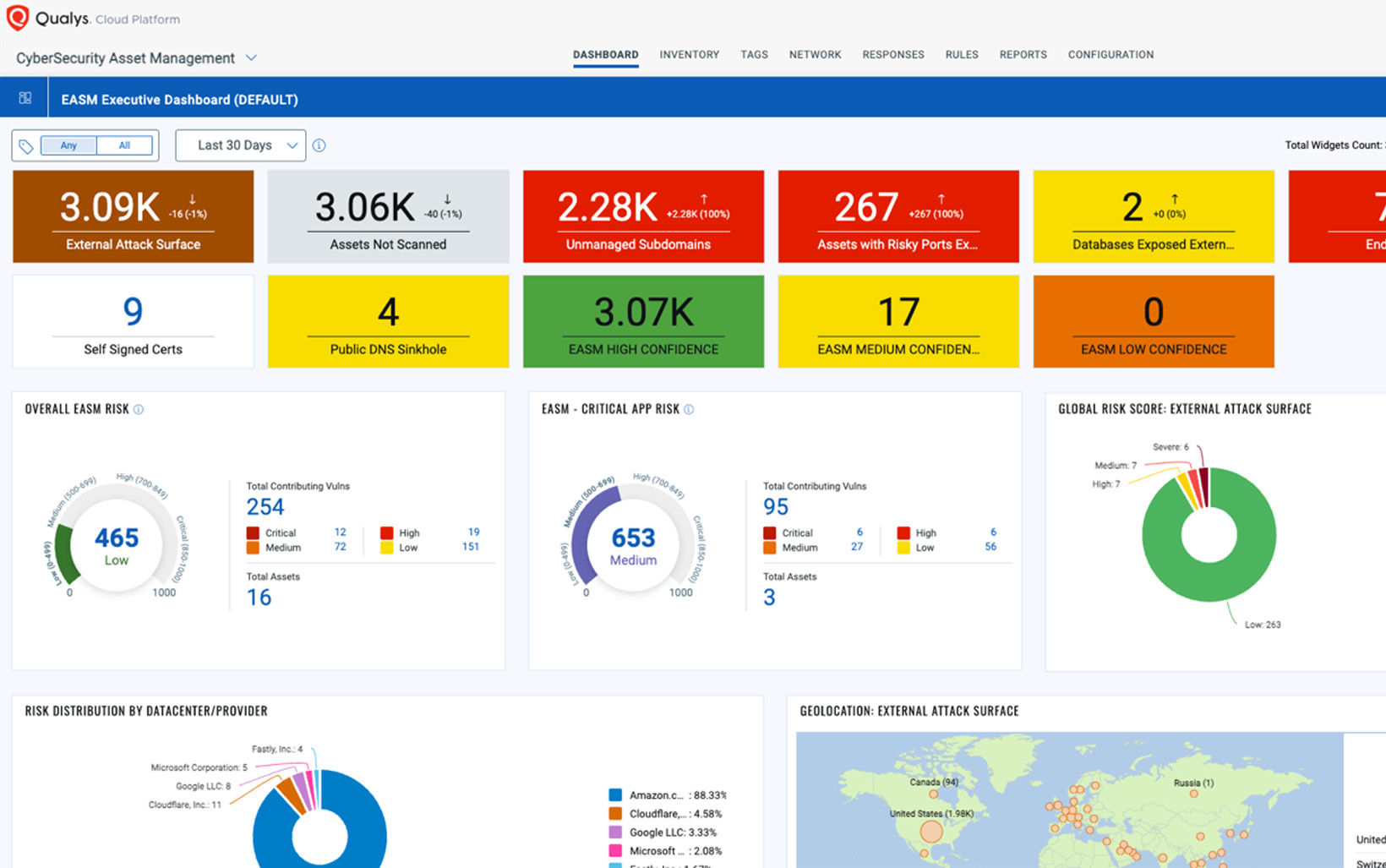
Coverage for Entire Attack Surface
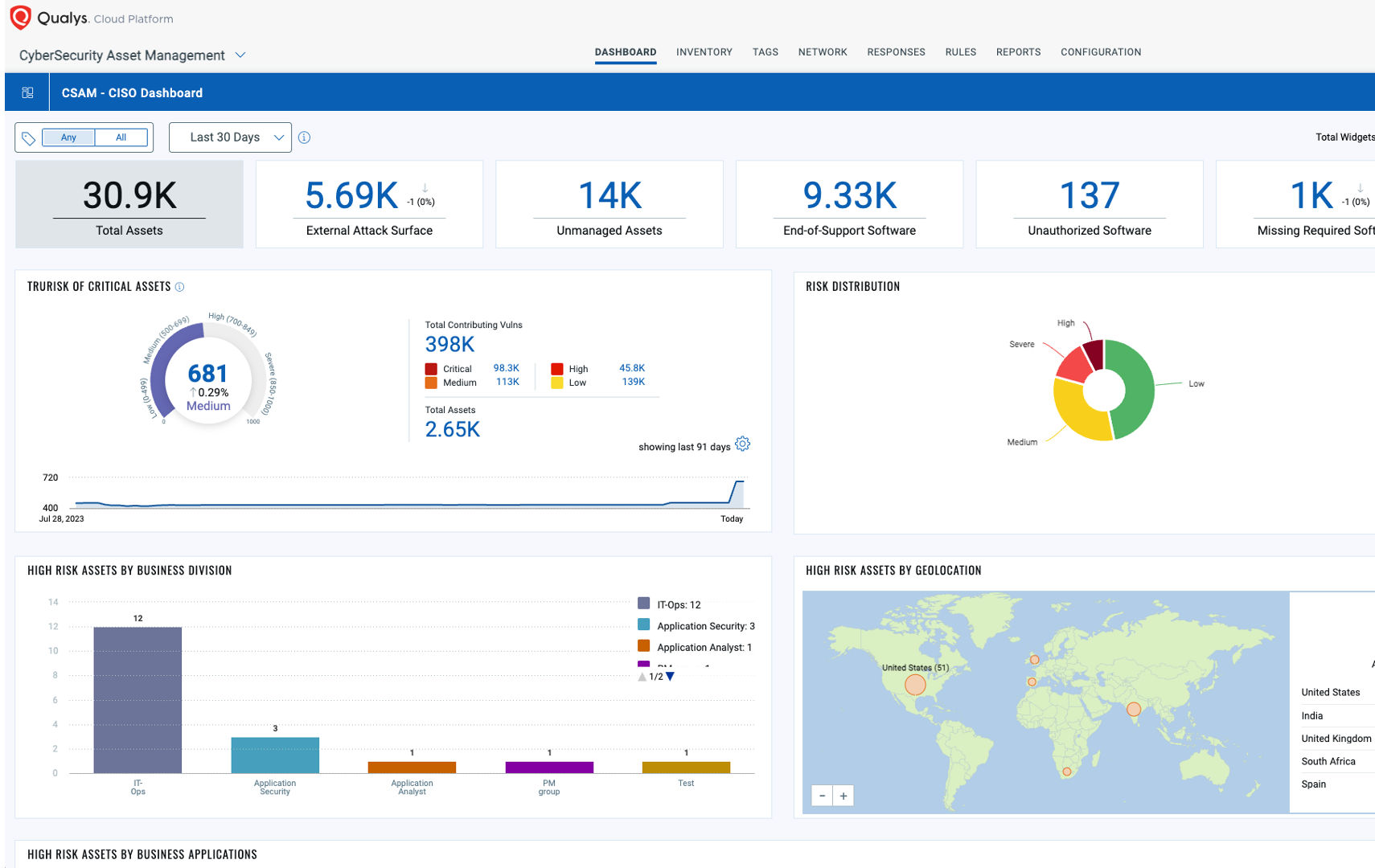
Over 30% of your assets are unknown to your VM program. Find them before the attackers.
Vulnerability & Configuration Assessment
Automate vulnerability & compliance reporting. Reduce zero-day and critical vulnerability detection times by 24% over competing solutions.
Risk-based Prioritization & Reporting
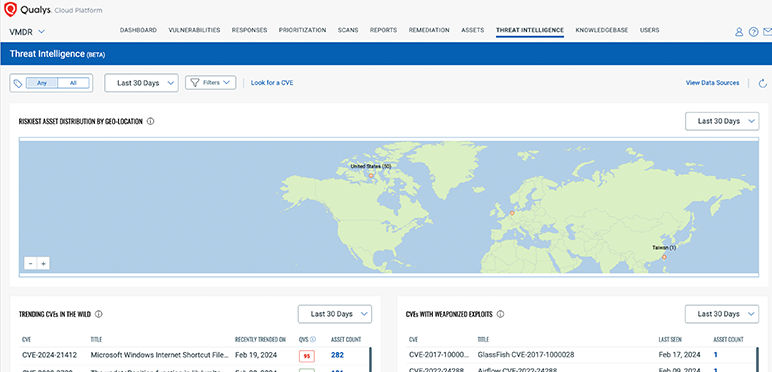
Prioritize vulnerabilities exploited in the wild by ransomware using TruRisk™ and MITRE ATT&CK®. Reduce critical vulnerabilities by up to 85%.
Automated Response
Deploy patches or mitigations directly or automatically generate tickets in your ITSM solution to reduce MTTR by up to 60%.
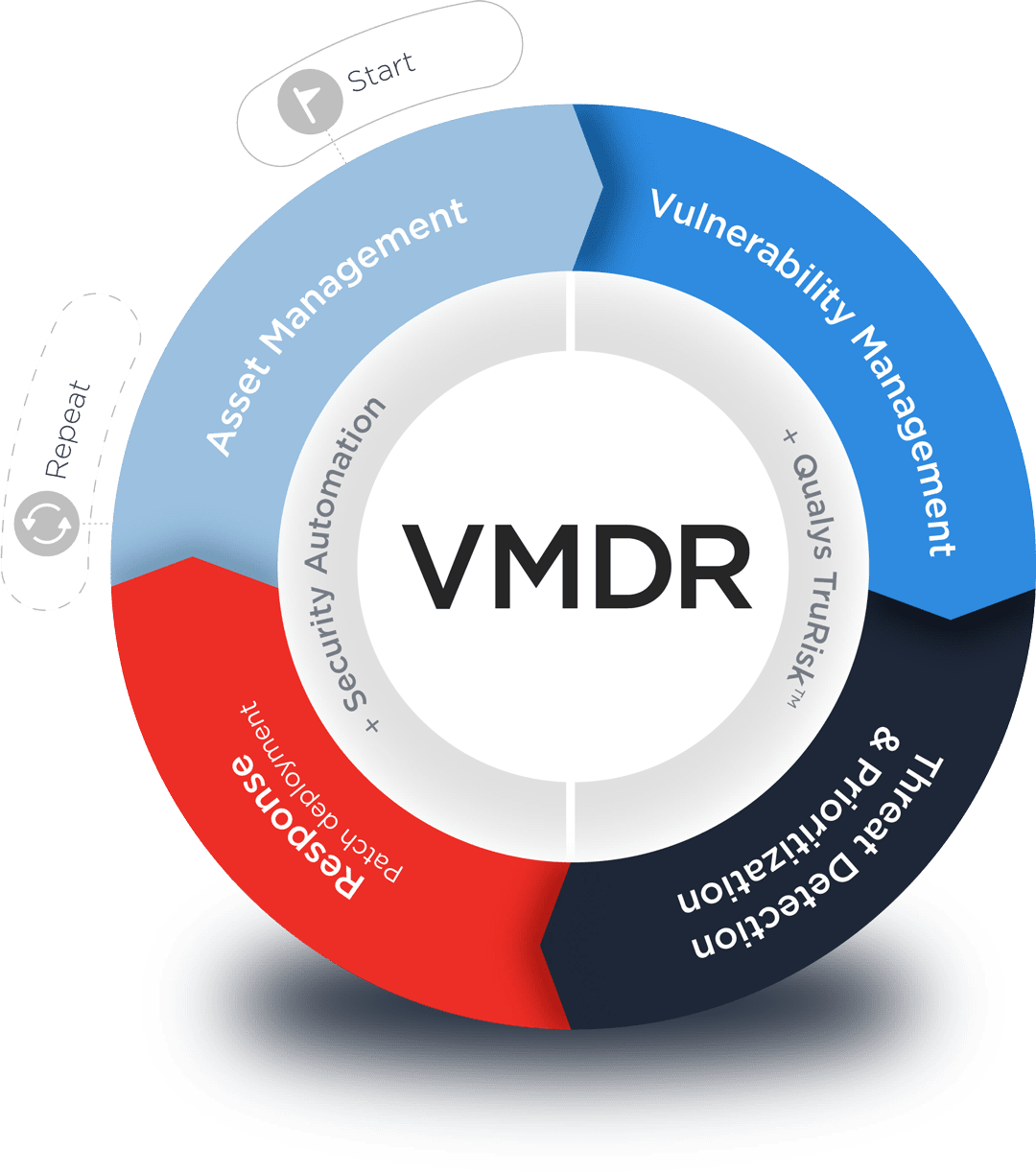
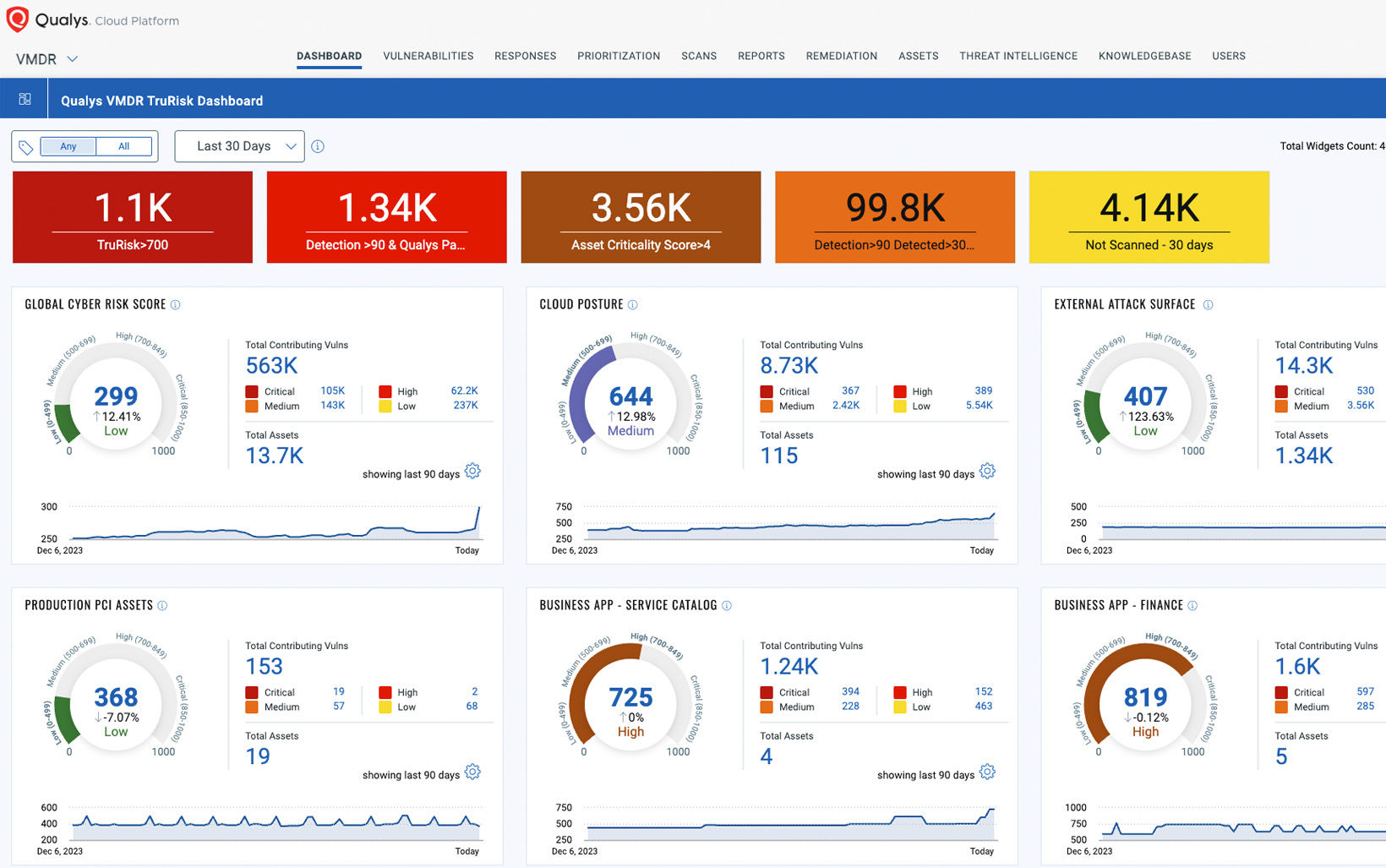
Detect and prioritize with risk scores you can actually trust.
Modern vulnerability management is more than just a list of detections and CVEs. Prioritize using TruRisk™ with Real-Time Threat Intelligence and remediate within a single platform.
Find every asset and every risk factor in context
Whether on-prem, in the cloud, or internet-facing, find your known and unknown assets automatically and scan them within a single platform.

Detect the critical CVEs you’re missing today
Improve coverage by over 30% with 100K+ identified CVEs and 190K+ detections along with 25+ sources of Real-Time Threat Intelligence and 98.7% coverage of CISA KEV to ensure nothing falls through the cracks.

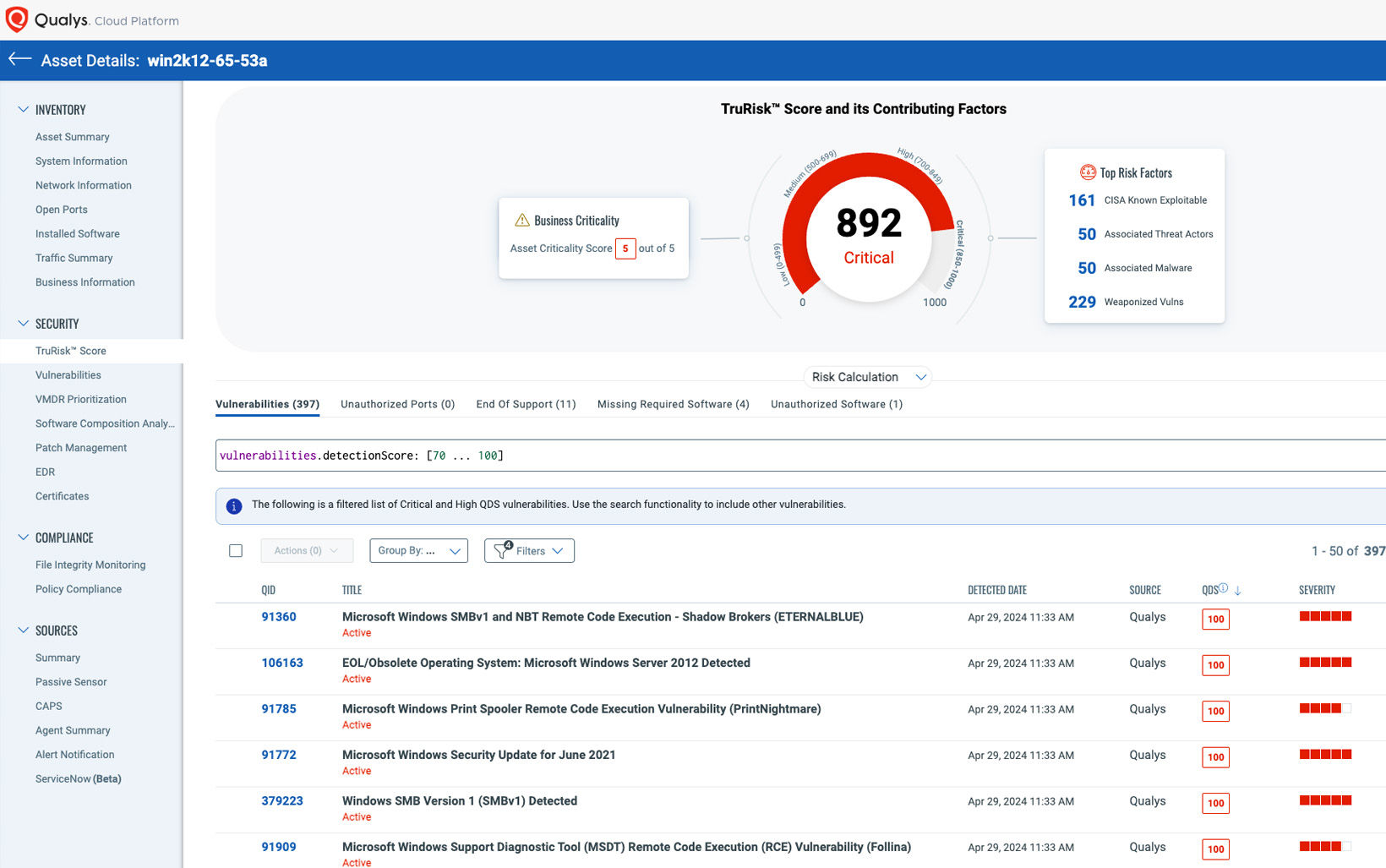
Prioritize using both threat and business context with TruRisk™
Combine asset criticality with context from the “Four E’s”—exposure, exploitation, evidence, and enterprise business context. The result is hyper-focus on business-critical risk and tailored remediation plans.

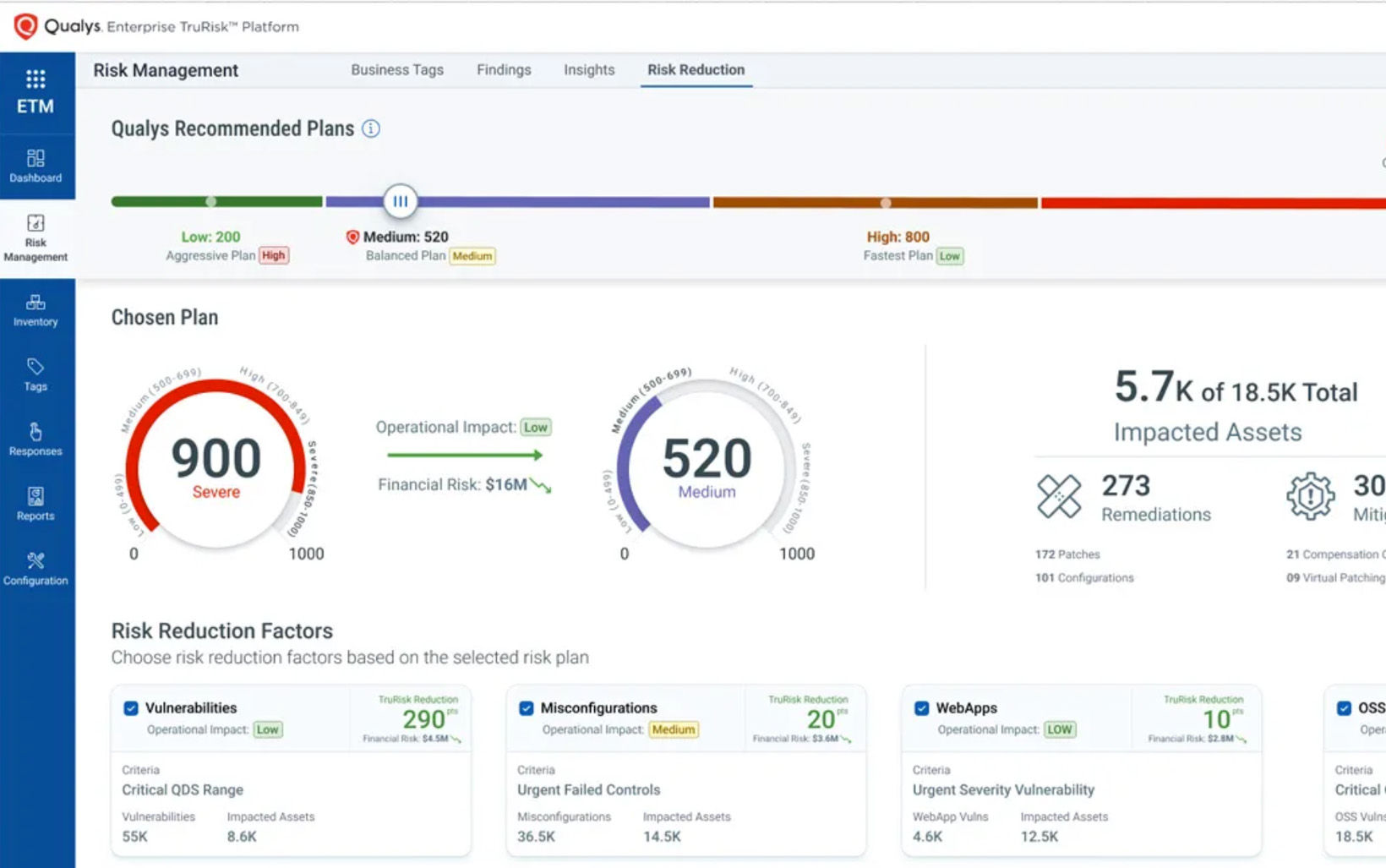
Eliminate critical risk in a single platform
Ditch the siloed patch solutions with tailored remediation plans, mitigations, automated patching, and ITSM ticketing integrations. Eliminate risk 60% faster to stop attackers before they start.

Share the “State of the Union” with Executives
Understand your organization’s risk landscape and implement prescriptive actions to mitigate risk with the TruRisk™ Executive Report.

More Than Just a “License to Scan”
Risk-based vulnerability management is more than a list of detections. Ditch your legacy scanner to measure business risk in the universal language of TruRisk™ with integrated VMDR includes:
- Asset and Vulnerability Management
- TruRisk™ with Real Time Threat Indicators and Continuous Monitoring
- Unlimited Virtual Scanners, Cloud Agents, Passive Sensors, Agent Gateways, and Container Sensors
- Runtime Software Composition Analysis
- Certificate Inventory, Assessments, & Renewal
- Cloud, Container, and Mobile Inventory
- QFlow (Rule Based Automation)
- Patch Detection and CVE Correlation
- PCI ASV Assessments including PCI 4.0
- CIS Benchmark Evaluations
- ServiceNow® ITSM and JIRA Integrations
Respond in months or respond in hours? The choice is yours.
- Map to every asset across your attack surface
- Detect and prioritize zero-day vulns faster
- Schedule and deploy patches natively
- De-risk your business FASTER

“Qualys scans it, finds it, patches it. That's it. In terms of time, manpower, planning, and the cost reduction in savings of labor dollars...huge.”


“VMDR detected ten times more vulnerabilities than in the same period the previous year.”

Explore VMDR Product Tours
Powered by the Enterprise TruRiskTM Platform
The Enterprise TruRisk Platform provides you with a unified view of your entire cyber risk posture so you can efficiently aggregate and measure all Qualys & non-Qualys risk factors in a unified view, communicate cyber risk with context to your business, and go beyond patching to eliminate the risk that threatens the business in any area of your attack surface.