Cloud solution for expanding VM programs with configuration scanning and simplified workflows to address configuration issues

Both vulnerability assessment and security control assessment capabilities are critical because many regulations prescribe technical control assessments (which drives SCA) and also explicitly prescribe vulnerability assessments.
Anton Chuvakin Research Vice President & Distinguished Analyst, Gartner
Qualys SCA Highlights
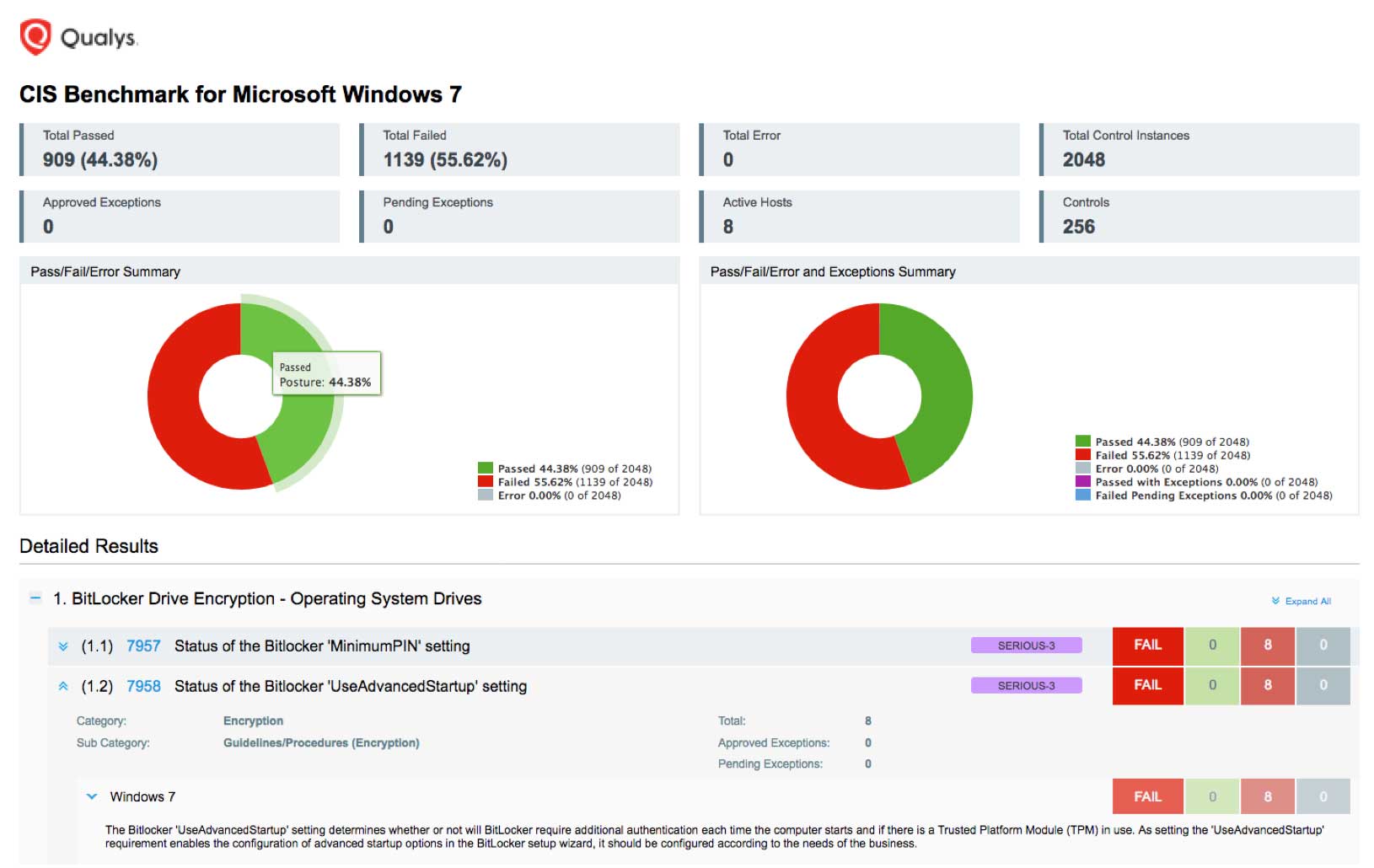
Augment your Qualys VMDR cloud service
Configuration assessment is an essential part of a comprehensive vulnerability management program. However, our competitors either combine lightweight vulnerability and configuration assessment, or offer the functionalities in separate products that aren’t integrated. Qualys gives you the best of both worlds. Qualys Vulnerability Management, Detection, and Response (VMDR) continuously scans and identifies vulnerabilities with Six Sigma (99.99966%) accuracy, protecting IT assets on premises, in the cloud and mobile endpoints. Qualys SCA, designed to work natively with Qualys VMDR, can be added seamlessly to your account with one click. Qualys SCA complements Qualys VMDR’s capabilities for detecting IT asset flaws with capabilities for assessment and reporting of configuration settings in 4 easy steps:
-
DEFINE: Import the applicable CIS policies in your subscription, and then customize the control values in the policy or policies per your security standards, or select/deselect the controls, all using Qualys SCA’s simple, web-based UI
-
ASSESS: Scan your IT assets and map the asset to the right CIS policy.
-
REPORT: Generate the report showing your control posture against the CIS Benchmarks, Qualys-provided remediation information, and the evidence for failure or passing, as well as the references to compliance standards. You can activate and deactivate controls as necessary for reporting purposes.
-
REMEDIATE: Remediate the failed controls, using Qualys-provided control remediation information.

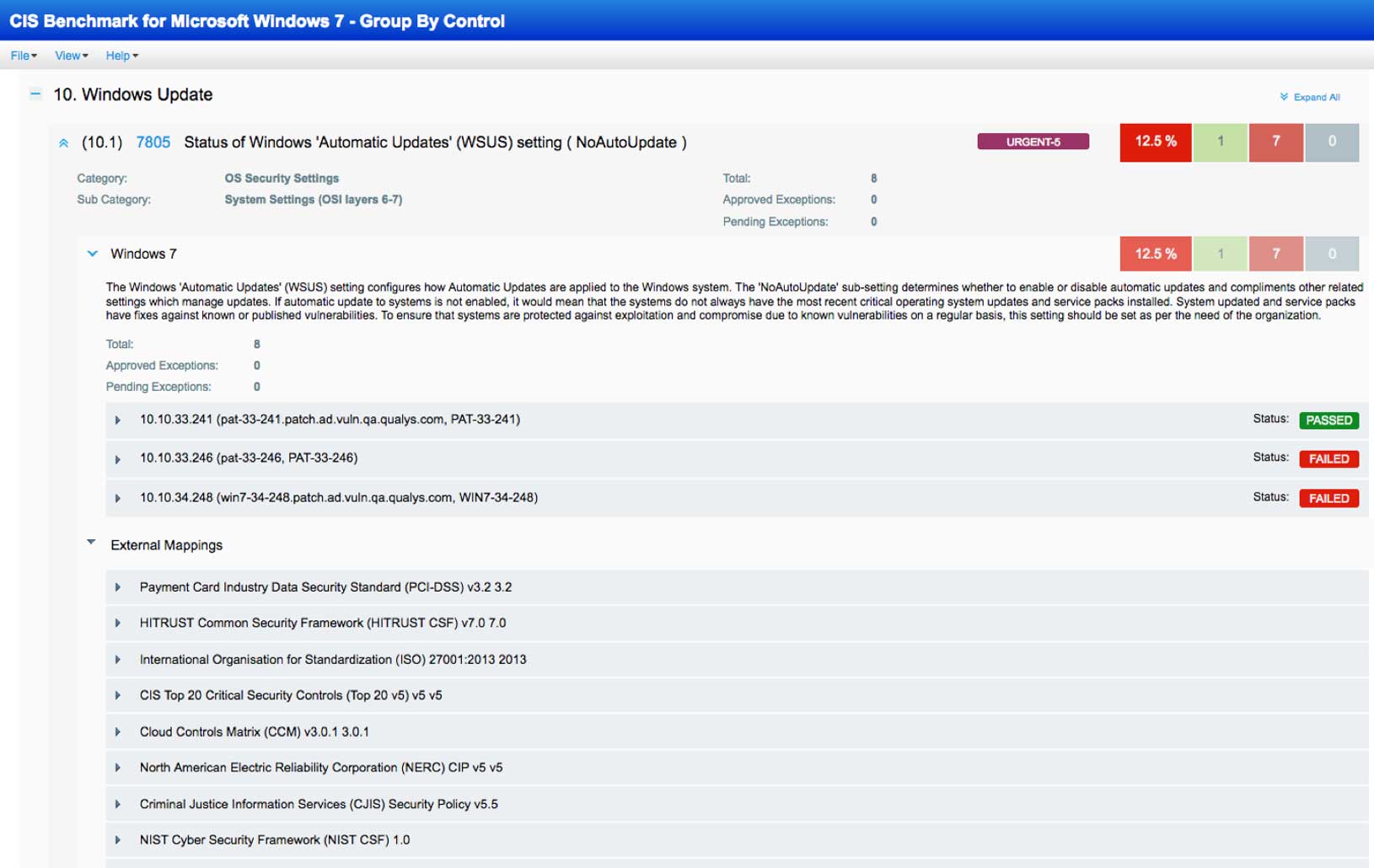
Perform configuration assessments quickly and comprehensively
Improperly configured IT assets put your organization at an increased risk for breaches. However, it’s common for organizations to rush systems into production with default settings and without basic hardening. Addressing these issues is key for data protection, regulatory compliance, and secure digital transformation initiatives.
With Qualys SCA, you’ll be able to automatically and continuously check that your IT assets — on premises, in clouds and on mobile endpoints — are configured securely according to CIS guidelines. This will give your organization a solid foundation not only for security but also for compliance with most regulations like HIPAA and with industry mandates like PCI-DSS.
Providing the industry’s widest coverage for CIS Benchmark technologies, Qualys SCA assesses the configuration of elements such as:
-
Operating systems
-
Server software
-
Cloud providers
-
Network devices
-
Desktop software

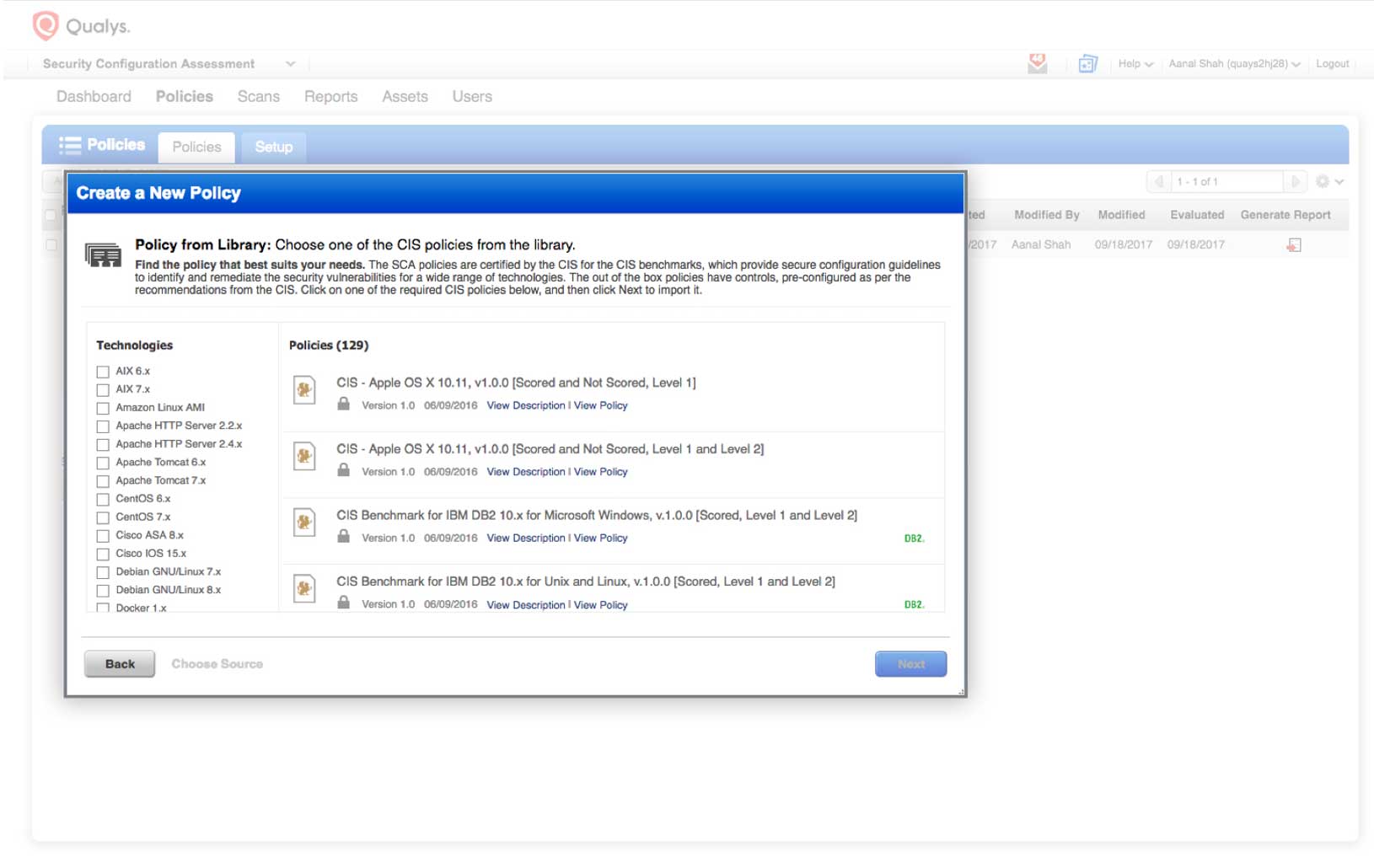
Leverage the knowledge of industry experts
Qualys SCA operationalizes the non-profit Center for Internet Security’s (CIS) Benchmarks by supporting them out of the box and automating the assessment of critical configuration settings on your IT assets against these guidelines.
The CIS Benchmarks , applicable to over 100 technologies and platforms, are unbiased and not motivated by profit considerations, and created via consensus by a community of international cybersecurity experts, including experts from Qualys.

Conduct remote scanning and auto-discovery of assets
Qualys SCA uses the same data collection technologies as Qualys VMDR, allowing for agent or agentless data collection, so that customers can comprehensively detect and better safeguard global endpoints, on-premises systems and cloud assets against today’s evolving cyber threats. Qualys data collection tools and processes cover all your bases and include:
- Physical and virtual appliances that scan IT assets located on-premises, in private clouds, or in virtualized environments
- Cloud appliances that remotely scan your infrastructure-as-a-service (IaaS) and platform-as-a-service (PaaS) instances in commercial cloud computing platforms
- Lightweight, all-purpose, self-updating cloud agents that reside on the IT assets they continuously monitor, with minimal network impact and no need for scan windows, credentials, nor firewall changes, with no need for the device to be on-line during your scheduled scanning windows.
Sharpen, simplify configuration assessments
With its benchmark-based guidance, simplified workflows for scanning and reporting, and cloud-based deployment, Qualys SCA provides a variety of advantages over competing products, especially legacy point solutions installed on premises:
- Lower cost of ownership because as a cloud service there’s no software to install nor maintain
- Improved protection of hybrid IT environments through the highly-scalable, extensible and centrally-managed Enterprise TruRisk Platform
- Consistent maintenance of a standard configuration throughout the enterprise via baseline configuration standards that can be applied prior to assets’ deployment
- Increased compliance and business effectiveness and efficiency, as well as stronger security posture
- Protection of the infrastructure and operations underpinning your organization’s key digital transformation efforts
See for yourself. Try Qualys for free.
Start your free trial today. No software to download or install. Email us or call us at 1 (800) 745-4355.
